Overview of Operational Risk and Resilience
Risk Introduction
Definition of operational risk by BCBS
- Operational risk is defined as the risk of loss resulting from inadequate or failed internal processes, people and systems or from external events.
- The definition includes legal risk, but excludes strategic and reputational risk战略风险和声誉风险.
- However, RPSMOR published in 2021: Where appropriate,strategic and reputational risks should be considered by banks' operational risk management.
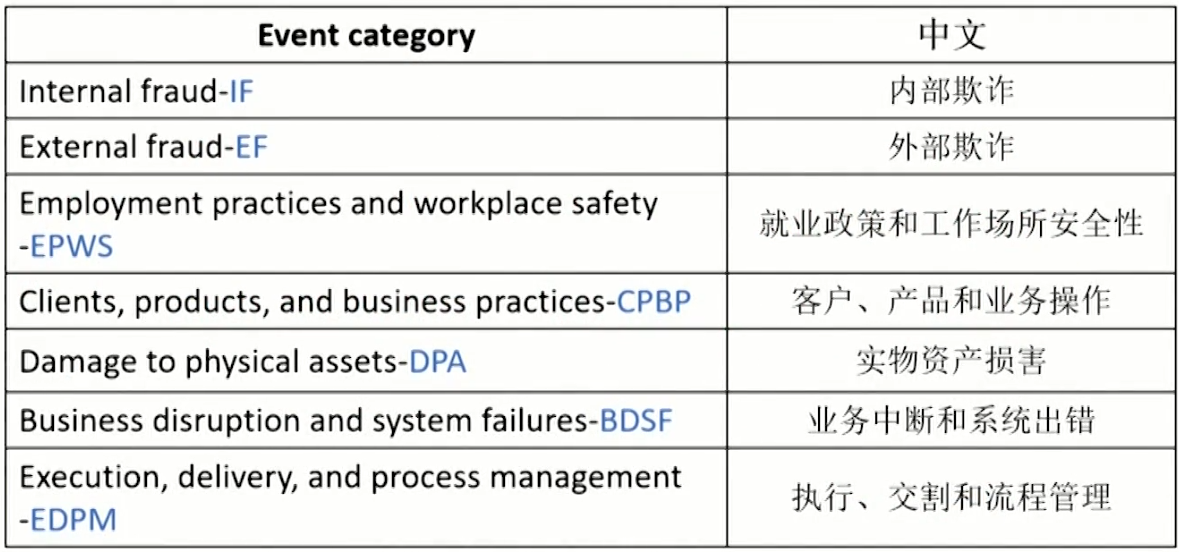
- Internal frauds (IF)
- Frauds committed or attempted by a firm's own employees.
- It include two sub-items: unauthorized activities, and theft and fraud (including extortion (敲诈勒索) embezzlement(挪用公款),misappropriation of assets (侵占资产),bribe(贿赂),etc.).
- External frauds (EF)
- Frauds committed or attempted by third parties or outsiders against the firm, common in retail businesses.
- It include two subitems: theft and fraud (such as check kitting and forgery(伪造)), and systems security(such as hacker attack).
- Employment practices and workplace safety(EPWS)
- More prominent in the Americas than Europe or Asia as either the labor laws are old-fashioned and there is more a culture of litigation against the employers.
- It includes three subitems: employee relations, safe environment, and diversity种族多元化 and discrimination.
- Clients, products, and business practices(CPBP)
- Losses from disputes with clients and counterparties,regulatory fines from improper business practices, or wrongful advisory activities.
- It includes client misinformation(错信息),complaints (投诉),and discounts(贬损)due to errors, product misspecification.
- Damage to physical assets (DPA)
- DPA involves all loss events related to natural disasters and human-made losses from sources such as terrorism and vandalism(故意破坏公共财物)
- The most common method to assess the exposure to this risk is through scenario analysis using insurance in formation.
- Very few firms actively collect losses on this risk type as these are usually either too small or incredibly large.
- Business disruption and system failures(BDSF)
- Losses from disruption of business or system failures, but is most difficult to spot
- Examples include IT breakdown, outages(停电)
- Execution, delivery, and process management(EDPM)
- Losses from failed transaction processing, as well as problems with counterparties and vendors.
- Examples include processing errors, missing documentation, vendor disputes.
Frequency and severity of seven events
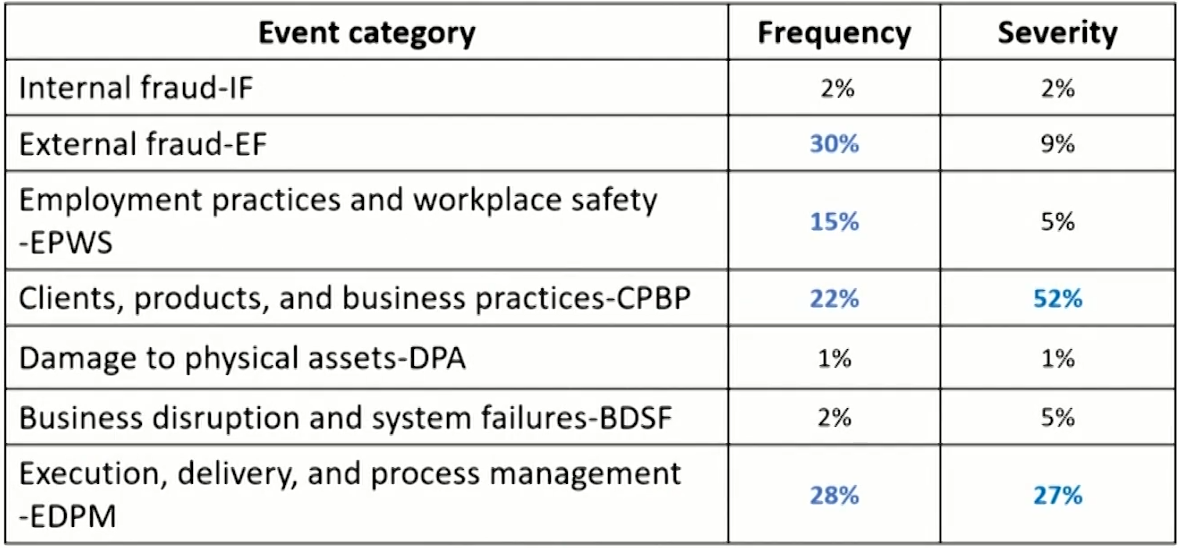
- CPBP category constitutes more than half of the operational losses from less than one quarter of event frequency.
- EF,EPWS, CPBP, and EDPM contributes to 75% of the frequency of operational risk events.
- CPBP and EDPM are enough to explain 79% of the severity.
- It's important to note that the numbers reported capture only the direct financial losses associated with each operational risk incident
- The indirect consequences of large operational risk events such as reputational damage, drop in market capitalization,management turnover, and remediation costs sometimes far exceed the direct financial cost.
Characteristics of operational risk
- Heterogenous异质性,都不一样
- Operational risk is a set of eclectic risks, with different causes, consequences.
- Even within a risk category,operational risk events can be very different.
- Idiosyncratic and diffuse特定原因的扩散的
- Operational risk types such as EDPM are driven or mitigated by the quality of a firm's processes and systems.
- Others such as DPA are often caused by external events.
- Heavy tailed肥尾的
- Operational risk materializes in the form of either a large number of small losses or a small number of large losses.
- Interconnected内在联系的
- Different types of operational risk are correlated because they may share common internal causes, such as weak internal controls, human errors, or poor risk culture etc.
- Dynamic变化的
- The nature and intensity of the many operational risk exposures depend on the activities of an organization or industry, and they evolve with these activities.
- The evolution of operational risk follows the development of the industry itself
Operational risk management (ORM) frameworks
- A representation of actions, techniques, or tools deployed.
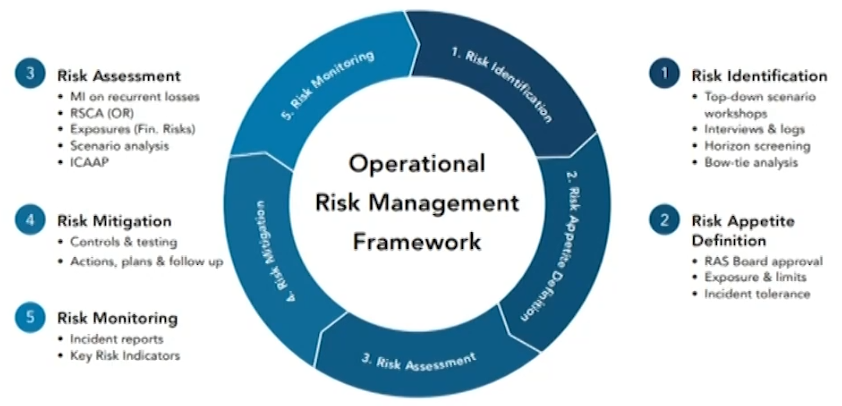
- Regardless of the representation, risk management frameworks narrow down to four main activities:
- risk identification
- risk assessment
- risk mitigation
- risk monitoring
- These four activities are usually represented by a continuous cycle appropriate to the iterative nature of risk management.
- Risk governance relates to the assignment of roles and responsibilities to execute and report on risk management.
- Risk culture and conduct relate to gaining the hearts and minds of everyone about risk management and good behavior.
- Risk appetite and tolerance is a requirement for regulated financial-services companies to define the limits of the risks they are willing to face in the pursuit of their objectives.
Operational resilience经营弹性
- Attention to resilience grew in late 2010s when the financial sector and regulators felt the need to focus on not only the financial stability, but also the operational stability, and ability to prevent and recover from operational disruptions.应对突发事件并恢复原状
- This attention emanated from the financial industry's critical dependence on IT systems, infrastructure and third-party providers.
- Operational resilience in UK
- UK releases the first regulatory guidance on operational resilience. UK Financial Conduct Authority(FCA), Prudentia Regulation Authority(PRA), and Bank of England(BoE) define operational resilience as the ability of firms and the financial sector as a whole to prevent, adapt, respond to, recover from, and learn from operational disruptions.
- Elements of operational resilience:
Continuity of business services: To mitigate the risk of disruption of critical business provisions.
Important (critical) business services: Services that, if disrupted, would cause intolerable levels of harm to consumers or market integrity and to ensure the continuity of these services within tolerance levels.
Impact tolerance levels: The amount of disruption that could be tolerated in the event of an incident, similar to recovery time objective in business continuity planning.. Impact tolerance must include a time-based metric.Tolerance levels aim to help senior management and the board set their own standards for operational resilience,prioritize, and make investment decisions.
Management of disruption: The response to disruption,the maintenance of trust by key stakeholders, and clarity of communication in times of crisis are important elements that contribute to the stability of the system.
Lessons learned: After a crisis, lessons can be learned from internal accidents or from public events in other firms.
- Operational resilience in the USA
- In 2020, the Federal Reserve issued its Sound Practices to Strengthen Operational Resilience and viewed operational resilience as holistic result of different components of ORM.
- ORM is the central component of operational resilience.
- ORM has two specializations: third-party risk management,which is essential for the resilience of supply chains; and scenario analysis, for the necessary preparedness to tail events.
- Business continuity management (BCM) and IT systems resilience are two critical supporting pillars of operational resilience.
Risk Governance
BCBS Principles for the Sound ORM

- Culture led by the board of directors and implemented by senior management
- Maintenance of a sound and proportionate ORM framework(ORMF).
- Board review and approval of ORMF
- Risk Appetite and tolerance statement for operational risk to be approved and periodically reviewed by the board.
- Senior management role in ORM policies and systems development and implementation.
- Comprehensive identification and assessment of operational risk in material activities
- Change management process adequately resourced and articulated.
- Regular monitoring of operational risk profile and exposures.
- Strong control environment: internal controls, mitigation,training, and risk-transfer strategies
- Robust information and communication technology(ICT)management program, in line with ORMF.
- Business continuity plans预案 in place and linked with ORMF
- Public disclosures on approach to ORM and risk exposures.
Supervisory expectation on governance of ORM
- The fundamental expectation from regulators is that ORM should not be a mere compliance exercise of policies on paper,rubber-stamped by the governing body
- To protect against this risk of non-compliance, it is good practice to maintain a library of regulatory documents that govern how the operational risk framework should operate and ensure that all relevant staff are aware of their contents.
- Operational risk staff should be asked to confirm annually that they are fully aware of listed documents and contents.
Committee structure in risk governance

- The lowest level oversees activity by business or function
- The group operational risk committee oversees, manages,monitors, and reports the consolidated picture to executive/management committee and board risk committee.
- The board risk committee oversees all operational risk.
- Operational risk is often split into several risk categories, with each category having its own committee in many large organizations, subordinated to:
- either the board risk committee (or enterprise risk committee)
- or to the operational risk committee, reporting in turn to
the enterprise risk committee
Role of BOD in risk governance
- The board of directors is ultimately responsible for最终责任人:
- general administration of the firm.
- setting the risk appetite of the firm and for making sure that it operates within the limits of its risk appetite.
- establishing a risk management culture.
- validating the operational risk management framework and ensuring a periodic revision of the ORMF.
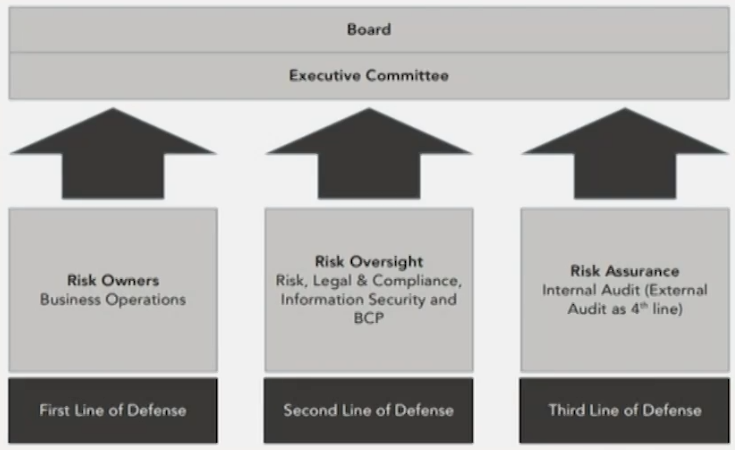
Three lines of defense model
- Line 1前台: This is the risk owners understood as the front line of the business, so-called business unit management.
- Line 2监督指导: This is an independent corporate operational risk management function(CORF) which provides guidance,oversight and challenge of the first line.
- Line 3审计: This is the internal audit function serving as an independent assurance challenging line 1 and 2. Internal audit should report in solid line to non-executive directors.
- Difference between line 1 and line 2
- The first line owns the final sign-off签字权 on risks assessment and controls, this is not the role of the second line.
- The first line owns the risks and the second line owns the methodology.
- Line 1.5: Risk specialists(risk champions or risk correspondents or stewards) in each business department to interact with the risk function which are particularly common in larger organizations.对接1和2的联络人
Risk Appetite
- Definition: The board is responsible for determining and defining the nature and extent of the significant risks it is willing to take in achieving its strategic objectives.

- It is the role of the board of directors to ultimately own the risk limits and to validate them periodically.
- In practice, the board often delegates this responsibility to the board risk committee, which in turn requests the support of the risk function to ensure the implementation of these limits in controls and exposure in the business, and to regularly report on them.
- Risk appetite governance
- Allocate a risk owner to each risk type labeled in the risk appetite structure.
Designate control owners and metrics owners for the various operational risks when the risk appetite sub-categories and controls cascade down into limits, controls,and monitoring metrics. - Risk owners are responsible for managing, maintaining, and monitoring the risks with the stated limits of appetite and tolerance. Risk owners are the first line of defense.
Controls owners are responsible for the design,implementation, and effectiveness of the controls.
Metrics owners are responsible for the collection, reporting and monitoring of the metrics capturing the performance of the organization with regards to risk appetite.
- Allocate a risk owner to each risk type labeled in the risk appetite structure.
- Regulatory expectations for risk appetite
- Easy to communicate and understand.
- In alignment with the bank's strategy, business plans and operations of the firms.
- Risk limits should be monitored through indicators related to risk exposure, control environment, and loss events.
- Risk appetite should be forward-looking and subject to stress testing and have a view of what events might push the bank outside the limits of risk appetite and tolerance.
Risk culture
- Culture is the summation of values and ethics, desired conduct standards, and implied behaviors. While cultural norms and beliefs can't easily be measured, the conduct and behaviors that the culture norms can be observed, monitored,managed and incentivized. Conduct and behaviors are the only visible elements of culture.
- Risk culture
- In the eyes of regulators, risk culture is closely associated with good conduct and ethics, and falls under the responsibilities of the board.
- Principle 1 by BCBS: The board of directors (BOD) should take the lead in establishing a strong risk management culture.
- The board of directors must lead the risk culture to be implemented by senior management. This is referred to as"tone at the top"
- Risk culture is supported by management reinforcement of:
Codes of conduct and ethics.
Compensation structure.
Training to raise awareness of operational risks.
- Codes of conduct and ethics
- Reinforcement of adherence to the code of conduct and discipline are effective ways to influence behaviors.
- But unnecessary blame should be avoided. A "no-blame culture" along with "tone from the top" is the most common recommendation for the establishment of a good risk culture.
- Compensation structure
- Toxic risk cultures are often triggered by overambitious short-term growth and profit targets, undue pressure on staff and management, and resistance to bad news.
- Aggressive compensation structure like that the bank increases the proportion of incentive compensation for its traders and investment bankers should not be recommended.
- Training
- induction training for new hires
- online modules available to all staff
- specialized training for the risk function
- Signs of good risk culture
- applicability of the rules to everyone
- swift escalation上报 of issues
- sharing of the lessons learned
Risk Identification
Scope of risk identification
- Top-down: Start from the senior leadership, then down to business units, and finally to individual business processes.
- Target: Aim at identifying key organizational risks, the major business threats that could jeopardize strategic objectives.
- Outcome: Risk prioritization and risk ranking is an important outcome of top-down risk identification.
- Bottom-up: It complements top-down approach. Businesses and divisions evaluate their own operational risk.
- The reconciliation of top-down and bottom-up generates a comprehensive view of the operational risk profile.
Top-down
- Business-specific risk identification
- Exposure drives impacts in risk, should a failure materialize in one of these activities.
- Vulnerabilities are the weakest links in business activities. These can be inadequate or outdated products, systems overdue for maintenance and testing, non-core businesses left unmonitored.
- If vulnerabilities are aligned with large exposures, this can result in very significant losses or a failure of the business.
- The benefits of listing exposures and vulnerabilities as a risk identification brainstorming method has the main advantage of being business specific.
- The risk wheel
- The risk wheel is a classic brainstorming tool to encourage creativity and ideas during risk identification workshops.
- Domino effect: Salary cut down → personal effectiveness → delays or descoping of project IT upgrade → IT risk materializes → systems disruption → impact business continuity → reputational damage.
- Emerging risk identification: horizon scanning
- Known emerging risks: such as cyber, compliance, and climate change. In this, "emerging" means "increasing.
- Nascent新生 emerging risks: just starting to appear on the risk radar of a community or of an organization and truly deserve the term of emerging risk.
- Benchmarking pieces of information can be used for inspiration or as a checklist.
- A way of scanning horizon risks is PESTLE analysis:
Political
Economic
Social
Technological
Legal
Environmental
Bottom-up
- Event and loss data analysis
- Internal losses: Repeated internal losses might be a sign of failure in the internal controls system.
- External losses: Such as consortium data.A best practice is to monitor all large incidents communicated by peers and ask objectively: "Could this incident happen to us?"
- Near misses侥幸逃脱: Incidents that could have resulted in an operational loss but did not because of good luck or outside intervention. Near misses are "lessons for free".
- Risk and Control Self-Assessment (RCSA)
- An organization, a business line, or a department evaluates the likelihood and the impact of its operational risks. This gives information on the level of residual risks.
- RCSA is often workshop-style discussion facilitated by the second line to collect information from the first line.
- In the largest institutions, the process can take the form of questionnaires.
- Selecting the relevant participants: Two types of employees are suitable to interview. One group is the most experienced employees.The other group comprises recent hires.
- Frequency of RCSA: typically performed annually, updated after each trigger event in mature firms. If performed too frequently, the process can turn into a box-ticking exercise.
- If too granular, the output will be a collection of small daily risks and inefficiencies that are not always of much value. People may miss the big picture when it comes to risks.
- Process mapping
- Lay out the tasks of a process, step by step,and asking what can go wrong in each step. This exercise highlights possible under-control or over-control of risks.
- For process mapping, appropriate analysis is important:
If too granular, the process mapping will be excessively time-consuming and likely to raise only minor issues.
If too high-level, it won't be informative enough to be used.
Scenario analysis- Brainstorming techniques
- The regulatory guidance document describes scenario analysis as an exercise of extreme events identification, using workshops and brainstorming techniques.
- Brainstorming techniques are a method to identify,analyze and measure a range of scenarios, including low probability and high severity events.
- The preparation phase: Firms are required to minimize subjective biases when conducting scenario analysis.
- The participants in scenario analysis workshops should be senior managers within the different business functions with experience and understanding of the risks.
- The involvement of additional external experts is advisable to help mitigate some biases such as myopia目光短浅, excessive focus on scenarios driven by external causes.
- The generation phase: aimed at producing a long list of scenarios to be considered.
- The intermediary phase: Scenario selection in which some scenarios are consolidated合并, and others eliminated or added.
- An example of consolidated scenarios are those relating to the same internal impact but different external causes.
- It is useful to compare the bank's scenarios with an industry scenarios, to determine whether omitting relevant scenarios.
- Some scenarios can be eliminated if the risk owner can convincingly demonstrate that the maximum loss generated by a given scenario is moderate enough to be absorbed by operating margin and without significant disruption.
Examples of risk taxonomy分类
- Basel taxonomy
- Level 1 is the highest-level category;
- level 2 is a detailed version of level 1;
- level 3 provides examples.
- The BCBS only recognizes the first two levels as regulatory categories.
- The number of risks to assess, manage, and report needs to be kept at a reasonable level. Too much detail is detrimental to the quality of information, difficult to review,and can drain resources.
- ORX taxonomy
- The taxonomy revises the Basel operational risk taxonomy
- The taxonomy does not radically depart from the Basel categories but offers some noticeable modifications:
It presents 14 level 1 risk types compared to 7 from Basel, and some level 2 risks have been elevated to level 1 given their prominence in today's world.
Structure of taxonomies
- Best practice is to distinguish and separately categorize the different components of uncertainties: causes, risks,impacts,and controls which are organized in taxonomies.
- A structure of taxonomies of causes, controls, risks, and impacts, circling the actionable part of risk management: acting on the causes and the controls.
- Causes and controls are the prime objects of risk management actionability.
- It is neither reasonable nor economically efficient to attempt to eliminate every risk. However, trying to eliminate the downside of a risk while preserving its upside makes sense.
- To limit the downside of operational risk, organizations and individuals can, first, act on their causes and, next, apply controls on the remaining causes, to limit the two dimensions of a risk-the likelihood and the impact.
- Cause taxonomy
- The natural level 1 causes for operational risk events by BCBS are PPSE, which is most common method adopted by the market.
- But not every bank refines the categories to finer level 2 which provides useful insights into the causes of incidents.
- Impaet Taxonomy

- Control taxonomy
- Preventative control
- Detective control
- Corrective control
- Directive control
Risk Measurement and Assessment
Loss data collection
- In 2000, ING created its first representation of the ORM framework. It comprised four concentric circles:
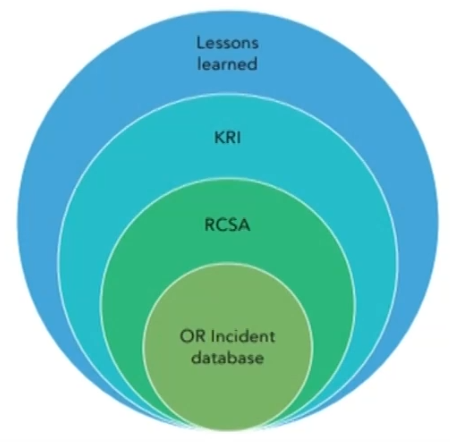
Incident database
- Incident data collection (internal and external)
- Comprehensive data
- Dates of incidents and settlement lags
- Data quality requirements
Comprehensiveness of data
- Basel committee does not define "material activities and exposures," but sets a minimum threshold for loss reporting at £20,000(about $22,000).
- From a regulatory perspective, the choice of the reporting threshold should not affect the credibility of the process nor impair management information.
- It must be justified and should not suggest "cherry-picking" or manipulation of capital requirements.
- From a regulatory perspective, firms must only report incidents leading to financial losses.
- From a management perspective, it is good practice to record also the so-called "non-financial impacts," such as reputational damage, customer detriment, disruption of service, or management time and attention.
- "Non-financial impact is particularly misleading because the indirect consequences of many material operational risk events have financial implications: Regulatory scrutiny,customers'dissatisfaction, remediation plans, and management attention all have costly consequences.
- When these repercussions are not properly quantified, the cost of operational risk can be significantly underestimated.
- Grouped losses汇总 are distinct operational risk events connected through a common cause
- Examples of grouped losses: the same wrong advice given to a group of clients, leading to a series of compensation claims.
- Different events that materialize from a single failure must be grouped as a single loss to reflect the same underlying cause.
Dates of incidents
- Date of occurrence: when the event first happened
- Date of discovery: when it is first identified
- Date of reporting: when it enters the reporting database
- Date of accounting: when the financial impact enters the GL
- The difference between occurrence and discovery reflects the visibility of issues, whereas the difference between discovery and reporting shows how diligently勤勉 operational incidents are reported to the risk function.
- Include a maximum allowed time for reporting incident.
- Best practice dictates a risk-based approach that will not waste resources by rushing to report immaterial events.
- Material incidents must be reported within a few working days, while minor incidents can be included in periodic summary reporting.
Data quality requirements
- Reconciling对得上 the loss data recorded as operational losses with information from other sources. These sources often include the general ledger (GL) that captures all cash inflows and outflows of a firm, including unintentional losses and gains.
- GL is no substitute for a dedicated operational event database because it only captures the direct financial losses or accidental gains, but it does not link the indirect effects.
- Underreporting is a challenge. Corporate incentives to report operational incidents range from soft encouragement to stringent oversight.
- Self-reporting of incidents is required, apply disciplinary action if unreported events are subsequently discovered.Most organizations include risk metrics in the balanced scorecard of their managers, as part of a risk-based performance system, a practice encouraged by regulators.
Qualitative risk assessment
- Risk and Control Self-Assessment (RCSA)
- Key performance indicators(KPIs), Key risk indicators(KRIs),Key control indicators(KCIs)
Risk and Control Self_Assessment (RCSA)
- The RCSA refers to evaluating the likelihood and impact of operational risk faced by a business including both the firm's risk exposures before the impact of existing controls has been assessed (inherent risks), and those that remain after the evaluation of the controls in place (residual risks).
- Variations on the RCSA include the risk and control assessment (RCA) and the residual risk self-assessment (RRSA).
- RCSAs are qualitative and largely judgement-based.
- RCSAs are often conducted as workshop-style discussions.
- Some firms may form a dedicated risk assessment unit (RAU),responsible for the conduct of RCSAs. An RAU can be a part of a business line, division, or an organizational process.
- Mature organizations back-test the results of risk assessment against past incident experience.
Likelihood and Impact
- Severity assessment: impact scales
- Four types of impacts: financial, regulatory, customer, and reputation.
- Likelihood assessment scales
- Likelihood scales are either expressed in percentages of likelihood or frequency of occurrence ("once in x years").
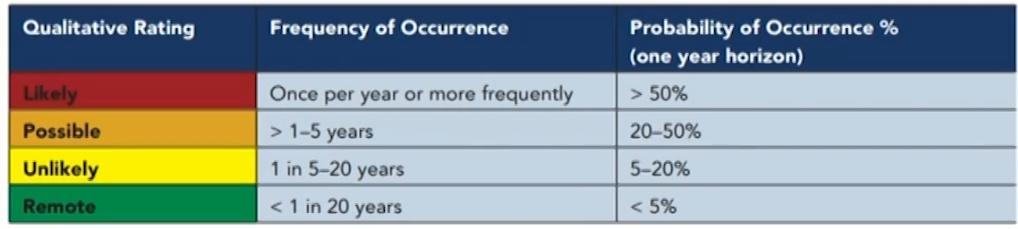
- Likelihood scales are either expressed in percentages of likelihood or frequency of occurrence ("once in x years").
- The various combinations of impact and likelihood are attributed colors that reflect the intensity of the risk. The colors used are red-amber-green or red-amber-yellow-green
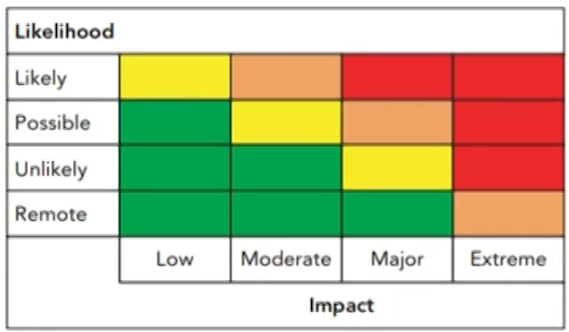
Outcome of RCSA
- The results of assessments must be documented and submitted to business line managers for approval and sign off.
- Action plans are owned by the first line (business-line managers) rather than the second line. Line managers are responsible for implementing mitigating action plans.
- Line managers and risk managers could expect to get from an RCSA exercise a view of residual exposure to key risks, when risks assessed as such are deemed above risk appetite, they will be the object of an action plan.
Challenge of RCSA
- The first challenge: Subjectivity of judgments, behavioral biases, and limited data input can quickly impede the quality and reliability of output.
- The second challenge: Difficulty in achieving comparable results across different assessment units, different departments, and businesses, often assessed by different people.
Key Performance Indicators (KPI)
- KPIs measure performance or target achievement.负激励
- Examples of KPIs include:
- Maximum downtime/uptime of IT systems
- Error rates on retail transactions
- Client satisfaction score/Level of client complaints
Key Risk Indicators (KRI)
- KRIs are monitoring metrics that signal the increase/decrease in the level of risk, either in potential impact or in likelihood.
- Examples of KRIs used in measuring likelihood include:
- Increase in number of transactions per staff (risk of errors)
- Drop in customer satisfaction scores (risk of client attrition)
- Increase in the level of sales required for sales staff to achieve a performance objective (risk of fraud)
- Examples of KRls measuring impact include:
- Increase in the level of proprietary company knowledge held by a key employee (higher impact of discontinuity/loss of knowledge in case of departure/sickness)
- Increase in sensitivity of data held on given server (higher impact in case of data leakage/loss)
- Increase in value generated by top-10 clients (higher impact in case of client attrition)
Key Control Indicators (KCI)
- Key control indicators (KCIs) measure the effectiveness of controls, either in design or performance.Examples of KCls:
- Missed due diligence items
- Lack of segregation of duties
- Overlooked errors in four-eye checks (reviews by two competent individuals)
Interaction among KPls, KRIs, and KCls
- KPIs, KRIs, and KCls overlap in many instances, especially when they signal breaches of minimum standards
- The failure of a control function is jointly a KPl, a KRl, and a KCI.
- A poor performance will often become a source of risk.
- A key control failure always constitutes a source of risk.
- KRI thresholds and governance reflect the risk appetite and tolerance levels of an organization.
Quantitative risk assessment
- Causal analysis of scenarios情景分析
- Causal analysis is used to quantify operational risk scenarios,which focuses on tails (rare events) that affects the firm significantly.
- Causal analysis is based on forward-looking (not past) determinants of impacts and likelihood of operational risks.
- Quantitative risk assessment is important but challenging task in risk management when it comes to scenarios.
- Fault Tree Analysis (FTA)树图
- Fault trees decompose failure scenarios into external conditions and internal conditions.
- FTA is built upon a series of conditions that can either happen simultaneously (known as "AND conditions") or alternatively
- If conditions are independent, likelihood of this risk materializingis: P1P2P3P4P5.
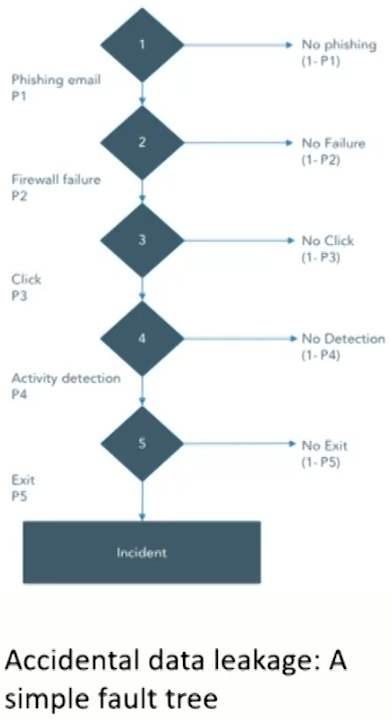
(known as "OR conditions").
- FAIR methodology因子分析
- FAIR(factor analysis of information risk) is a factor model for quantifying operational risk, which is based on decomposition of the risk into their factors.
- The steps are as follows:
Identification of the risk factors and interrelationships
Measurement/metric of each factor
Computational combination of the factors - In this method, a scenarigshould have:
an asset at risk (asset of the scenario)
a threat community (who or what the threat is)
a threat type (nature of the threat)
an effect (losses resulting from materialization of the risk)
- Root-cause analysis and Bowtie tool领结
- It takes the form of the "5-why" analysis.
- Recommendations require the first line to perform root-cause analysis.
- The investigations should be challenged by the second line.
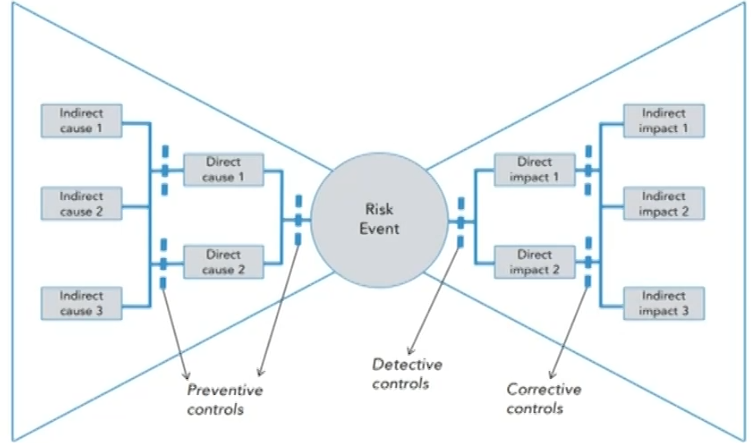
- Bowtie analysis is useful for:
assessment of the likelihood and impact of risks.
better understanding of the causes of risks and the possible failure of controls that may lead to their materialization.
investigating how quickly an incident is detected and how well the organization reacted in limiting the impacts.
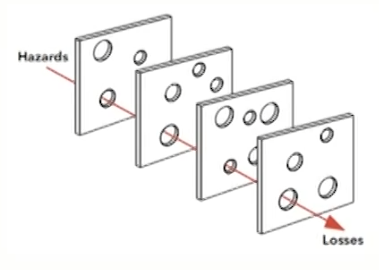
- Swiss cheese: control layering
- It is also called the cumulative act model. Each defensive layer are like slices of Swiss cheese, having many holes, which are continually opening, shutting, and shifting their location. The presence of one hole does not cause a bad outcome but does when holes in many layers momentarily line up
- In an effective control layering, where the holes are not aligned (failure rates of controls are independent), and controls compensate each other's weaknesses to produce a control system that works as a tight safety net, rather than like a row of dominos.
- Assessing independence of controls is at least as important as assessing reliability of each individual control.
Operational risks modeling and capital
- Loss Distribution Approach(LDA): Advanced Measurement Approach (AMA)
- Decompose a loss data distribution into two components: severity and frequency.
- Frequency and severity distributions are estimated independently and then convoluted into an aggregated loss distribution.The most common convolution method is Monte Carlo.
- Frequency(discrete) is modeled with Poisson distribution and negative binomial distributions.
- Severity(continuous) is modeled with log-normal distribution, Weibull and Generalized Pareto Distributions(GPD)(More heavy-tailed).
- Regulators require clear rules to be set for the selection of data and avoid "cherry picking" and manipulation of results.
- Internal loss data is the backbone of LDA because of more relevant to the organization.
- External loss data from peers can be supplemented.
- Mix internal and external data: Scale, Cut-off mix, Filter.
- Limitations and constraints of LDA
- The distributions of severity and frequency of operational losses are typically assumed to be independent
- Data are split into risk classes (or units of measure), where losses within each risk class should be iid (independent and identically distributed)
- LDA modeling Pillar 1 of regulatory capital are now being transferred to modeling Pillar 2 under ICAAP(Europe), as well as stress-testing calculations(USA) and operational resilience.
- The ICAAP is part of Pillar 2 of regulatory requirements which covers all financial and non-financial. So, ICAAP applies to all risks, not only operational risk.
- The lCAAP can inform the economic capital and both have the same purpose.
Quantification of operational resilience
- Differences between resilience frameworks and traditional business continuity management (BCM)
- BCM focuses on the continuity of each business process and recovery, in case of disruption within a given time frame (Recovery Time Objective, RTO).
- Resilience focuses on the continuity and recovery of important business services
- Key steps foroperational resilience
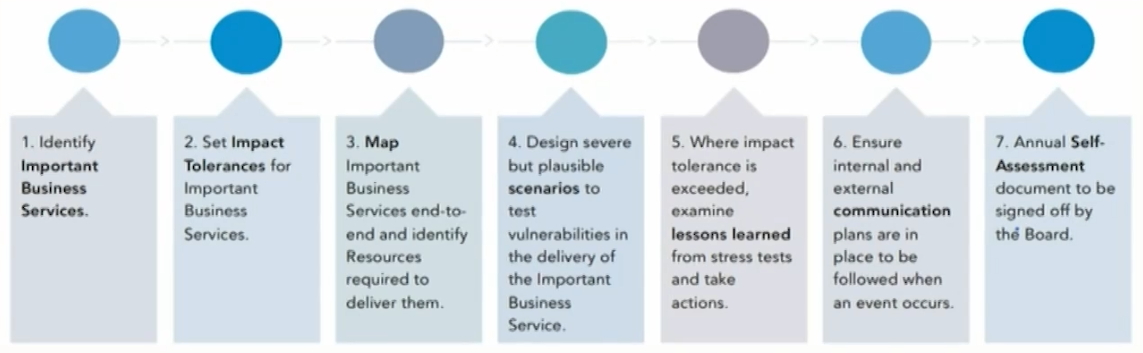
- Impact tolerances can be built up through business impact analysis (BIA).
- BIA is the assessment of consequences of disruption of a process or a service in business terms, but also on the resources needed to develop recovery strategies.
- The BIA report should prioritize the order of events排序 for restoration
- Business processes with the greatest operational and financial impacts should be restored first.
- Single points of failure(SPOF)单点故障 are relevant KRIs for resilience.
- One example of KRIs is the number of key employees without back-ups, without documented processes, with unique knowledge and skills.
- SPOF need to be mitigated and removed through back-up and redundancies, and if not, they need to be considered when setting tolerance thresholds and stress tests.
Risk Mitigation
Two kinds of operational risk
- Operational risks can be categorized in two types:
- External operational risks are those that arise due to the business environment of the organization or due to external events. External operational risks cannot be prevented, but they can be reduced.
- Internal operational risks are linked to people, processes,and systems. Internal operational risks tend to be far more preventable, largely through the use of internal controls.
Risk response
- Tolerate: accepting the risk as it is.
- Treat: encapsulating all the types of risk mitigation, mostly internal controls.
- Transfer: moving the risk to another party (external insurance).
- Terminate: removal of all risk exposure by discontinuing a product or ceasing operations in certain countries.
Internal control types
- Preventive预防 controls: intended to reduce the likelihood of an incident
- Segregation of duties职责分离
The front-office (trading desk) initiates trades, validated by the middle-office, confirmed and settled in the back office and treasury departments. - Access controls (digital or physical)
- Levels of authorization
- Process automation
- Segregation of duties职责分离
- Detective探测 controls: designed to alert if an incident occurs,accelerate its resolution, and limit the impact of the incident to the firm or its stakeholders.
- Exception reports
- File reconciliations
- Smoke detectors
- Intrusion detection systems
- Corrective纠正 controls: mitigating technique designed to lessen the impact to the institution when adverse events occur. They do not influence the likelihood of a risk happening, but lessen the pain if it does.
- Data back-ups
- IT systems patch management
- Continuity planning
- Systems redundancies
- Directive指导 controls: include all the prescriptions and rules to execute a process.
- Procedures and guidance manuals
- Internal training
- Team supervision
- Handover procedures
Control design
- Types of weakly designed controls include the following:
- Optimistic controls: Such as sign-offs for large volumes of documents before a deadline.
- Collective controls: Such as "four-eyes check" diluting accountability.稀释责任
- More of the same: Such as responding to a failure of collective controls by adding more controllers.
Control testing
- The main types of control testing are the following:
- Self-certification or inquiry询问: limited to secondary controls or controls related to low risk environments.
- Examination检查: This requires supporting evidence and documentation.The effectiveness depends on the relevance and adequacy of the documentation. It provides moderate assurance and is better suited for automated controls and sampling of manual controls.
- Observation观察: involves real-time oversight of the execution of the control process to judge its design and effectiveness.
- Reperformance重新测试: also called reproduction or parallel testing.The tester reproduces the control process on a sample of transactions and compares the results with those previously obtained by the process. It is the strongest form of testing.
Risk mitigation by process design
- Prevention through design
- Examples include checklists清单, communication protocols,standardization, and optimized work environments or systems design.
- Typology and mitigation of human error
- Lean Six Sigma
- Quality improvement
Typologyand mitigation of human error
- Skilled-based: slip
- Involuntary
- Caused by inattention, distraction, environment,tiredness.
- Controls: Improved, supportive environment re-engineered processes, adjusted pace, etc.
- Rule-based: mistakes
- Wrong action based on flawed rules
- Caused by wrong incentives, flawed products,misleading instructions, etc. One example is mis-selling to customers due to aggressive commercial incentives.
- Controls: change the rule
- Knowledge-based: mistakes
- Wrong choice of action facing a new situation
- Caused by lack of training, knowledge of the environment, causes and/or consequences of actions
- Controls: training, documented procedures, help file,escalation rules
- A fourth type is a violation
- Voluntary misdeed
- Controls for violations: Supervisory controls, either human or automated, through hierarchy, cameras, or automated recordings, improvements in risk and compliance culture that reward adherence to rules and processes
Lean Six Sigma
- Lean Six Sigma: DMAIC cycle
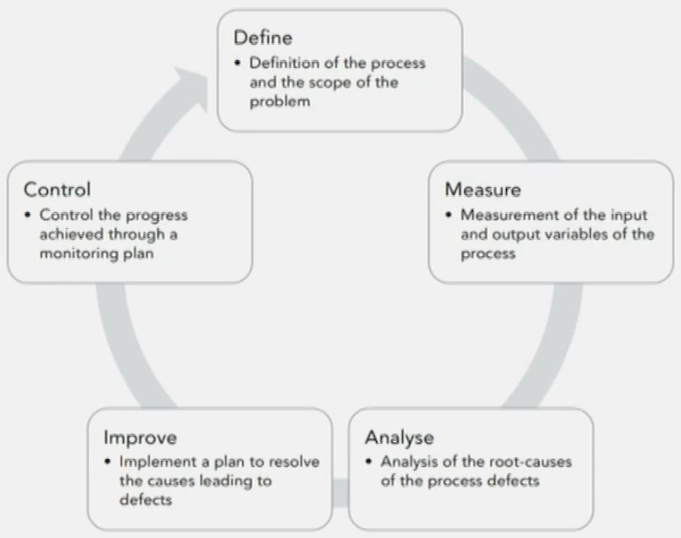
Quality improvement: represented by PDSA cycle.
- Plan: objective; questions and predictions; develop a plan to improve the model (who, what, where, when)
- Do: carry out the plan; document problems and unexpected observations; begin data analysis
- Study: complete the data analysis; compare data to predictions; summarize what was learned
- Act: what changes are to be made? next cycle?
New Product approval process
- Every project, product, and initiative in a business will bring novelty, lack of familiarity, and uncertainties that may generate significant operational risks.
- A common risk-mitigation approach is the New Product Approval Process(NPAP), and its generalization to new initiatives, New Initiative Risk Assessment Process (NIRAP).
- Best practice requires to present a business case to justify the allocation of resources. A proper business case would cover at a minimum five topics:
- Objective: what we want the firm to achieve and the rationale for the project.
- Alternative: Other options considered and reasons for selecting the current project.
- Expected benefits: Expected benefits and synergies from the project, and possible drawbacks.
- Commercial aspects: The costs, investment needs, and funding arrangements.
- Risks: Main risks and their possible impact on the business case and on the rest of the business, with their mitigation.
- Stages of involvement of risk function during a project's life.
- Initial stage(before kick-off): Risk identification and assessment. Mitigation and monitoring plans
- Project life: monitoring and risk update, regular meetings with the risk team and the project team to update risk identification and assessment findings for important and critical projects.
- Project closure: Debriefing, evaluations of project deliverables, analysis and documentation of the risks, lessons learned.
Mitigation measures to reduce impact
- Contingency planning应急方案 (Plan B)
- Contingency planning is a component of business continuity,disaster recovery, and of corrective risk management, the planning phase of corrective and directive controls.
- Specific forms of contingency planning are business continuity management(BCM) and disaster recovery plans(DRP).These are most relevant when we consider operational resilience.
- To be effective, the plan needs to be regularly tested, to ensure the practicality and speed of its implementation in case of an emergency.
- There must be a key owner who has clear responsibility for the design of actions and their execution, including communication with outside parties.
- BCM as an ongoing process
The first step is to ensure senior level commitment. Top-down direction, support, and ownership are essential in both the BCM process and the quick activation of the BCP when a crisis hits.
The next step is to initiate the management process and identify a team to take ownership as a continuing project,rather than a one-off event
- Resilience measurement
- Crisis management and communication
Event and crisis management
- To manage a crisis or a large operational event effectively,organizations need to demonstrate three essential qualities:
- Speed
- Competence
- Transparency
- In crisis mode, firms should have at a minimum two types of incident response teams:
- A technical team (or recovery team), composed of specialists who assess the incident and focus on restoring normal processes as quickly as possible.
- A communication team (external or internal), which deals with the media and the different stakeholder groups,including employees
- Four typical phases of a major operational risk event:
- Crisis
- Emergency response
- Recovery(RPO and RTO)
Recovery Point Objective (RPO) indicates the amount of data updated or created that will be lost or need to be re-entered after an outage.
Recovery Time Objective (RTO) is the amount of downtime a business can tolerate.The RTO is the maximum tolerable duration of disruption for a process, a system, or a service. - Restoration (back-to-normal)
Risk transfer
- Two methods to transfer risks:
- External Insurance保险: An organization agrees to pay a regular premium in exchange for being compensated should a certain risk materialize.
- Outsourcing外包: The process of delegating some of the company's tasks to a third party under a contractual agreement, such as IT server management, cloud computing, data centers, or call centers.
- external insurance
- For small losses: Many large institutions either self-insure small losses via a captive subsidiary自保保险子公司 or just absorb the volatility.
- For large losses: Financial institutions mainly use external insurance to cover extreme operational risk "tail" events, such as cyber risks, business discontinuity, or major class action lawsuits.
- Outsourcing
- For traditional banks: internalize credit decisions and allocations but outsource some of their ICT activities.
- For FinTech banks: more likely to manage their own technology platforms, but outsource credit risk decisions to other specialists.
- Outsourcing can increase or decrease the risk for an organization. depending on what process or activity is outsourced, to whom, and for which reasons.
- Outsourcing can result in increased operational risk labeled third-party risk. Increasingly, outsourcing is seen as a "risk sharing" activity.
Management of reputational risk
- Important elements such as reputational damage cannot reall2. y be outsourced (nor repaired) through insurance.
- Therefore, prevention and mitigation strategies are essential to build a solid reputation and to react quickly and appropriately in times of crisis to limit reputational damage following operational risk incidents.
- Some preventive controls and strategies are designed to build and maintain customer confidence.
- Detective controls, such as monitoring customer complaints on social media and tracking trends in refund requests or system downtimes, are designed to identify operational failures but also reduce their reputational impact.
- Many corrective risk controls and mitigation strategies are in place to protect the company's reputation and form actions taken when operational events hurt customers.
Risk Reporting
Roles and responsibilities of committees
- Risk Committee风险委员会
- Risk committee is authorized by the board to monitor the effectiveness of risk management framework.
- The risk committee will receive information on key risk indicators associated with the firm's risk appetite, the frequency and severity of risk events, and the investigation of the causes of large events etc.
- Any significant issues in control system or in operational risk status will be escalated to the risk committee.
- Reporting requirements related to the firm's operations must be sufficient for the board risk committee to determine that the organization's control and monitoring systems can effectively comply with, and operate within limits of, the firm's risk appetite, which is set by the board.
- Executive committee (ExCo)执行委员会
- Composed of elected board members and senior executives, acting as a steering committee for board.
- Facilitate decision-making during times of crisis and prioritize issues for the board to address during normal time.
- Oversee board policies, and ensure good governance practices.
- Oversee effective execution of the ORM framework.
- Audit committee审计委员会
- Responsible for a third level of operational risk oversight managed by the firm's internal audit activities (the third line of defense).
- Responsible for the assurance on the internal control system of the organization.
- Internal audit and audit committee have several cross-overs with respect to ORM activities.
Internal audit function regularly audits operational risk function and report findings to ExCo and audit committee.
Vulnerabilities in the control systems uncovered through internal audits are reported to audit committee.
- Operational risk committee操作风险委员会
- Central ORM function as a second line of defense centralizes most information regarding operational risk and its management.
- Central ORM function provide an aggregated view of various risks which are often managed in a siloed manner at the business-line level and their interaction.
- Central ORM function collects all relevant operational risk information from business lines to produce aggregated,synthesized reporting for operational risk committee and provide feedback to business lines, enabling them to:
monitor their own operational risks.
benchmark their performance relative to other business lines or departments, or to a firm-wide average.
Considerations of operational reporting
- Reports should be neither too large nor too small.
- If too large: significant risk of overlooking key pieces of information. Too much information can bury key insights.
- If too small: it can become meaningless.
- There is little uniformity in operational reporting across firms:
- Some focus on narrative of past risk events, others focus on forward-looking indicators. The more mature the ORM approach, the more forward-looking its reporting.
Seven elements of internal ORM report
- Seven elements included in internal ORM report:
- Top-10 risks and risk outlook in risk inventory
- Heatmap and risk register严重程度
- Risk appetite metrics
- KRIs and issue monitoring
- Incidents and near misses
- Action plans and follow-up
- Emerging risks and horizon scan finding
- Risk appetite metrics
- Risk appetite metrics (or risk appetite KRIs) are indicators reflecting the firm's compliance with risk limits for its operational risk appetite.
- At the business level, these metrics are collected and analyzed individually.
- When reported to upper levels of management and board,risk appetite metrics are presented as a single list.
- KRIs and issue monitoring
- KRIs can provide a granular, forward-looking analysis of risk exposure in different activities.
- Issues are grouped by business line or a major initiative (new business, merger etc.) to make reporting actionable.
- Incidents and near misses
- Increasingly, loss classifications are standardized and shared across financial institutions. One common standard is the ORX global banking loss-data service classification.
Although increasingly standardized, reporting thresholds may vary widely from firm to firm. - The materiality of an operational risk event must be judged not only by actual impact but also by potential impact.
Reporting thresholds for risk events and near misses should theoretically be based on potential impact of the event rather than its materialized impact.
Given the difficulty to estimate potential impact, firms and regulators use observed impact to set reporting thresholds.
- Increasingly, loss classifications are standardized and shared across financial institutions. One common standard is the ORX global banking loss-data service classification.
- Action plans and follow-up
- Action plans (including preventive, detective and corrective action plans) are risk-mitigation programs designed to improve the control environment.
- Action plans are tracked, reported by business-line owner.
- There is a zero objective for firms where risk management is strong: zero overdue actions and zero overdue audit recommendations.
- Emerging risks and horizon scan finding
- In a volatile environment, practice of horizon scanning to identify new trends and emerging risks has been instituted.
Emerging risks are reported regularly to risk committee.
Much of horizon scanning focuses on regulatory risks and changes in the compliance and regulatory environment.
Best practices suggest horizon scanning should reflect elements that could cause change in emerging risks.
- In a volatile environment, practice of horizon scanning to identify new trends and emerging risks has been instituted.
Characteristics and challenges of operational risk data
- Operational loss data are:
- heavy tailed or skewed statistically away from the mean.
- asymmetry with small number of large loss but large number of small losses.
- A proper allocation of risk management resources is to focus on the prevention and remediation of large incidents and not to be dispersed and distracted by daily volatility.
Ways to overcome these challenges
- Escalation报告 of large risk events to upper management.
- Identify and analyze regularly large number of small losses to detect a potential breach in control or a structural flaw in a process that would warrant an action plan.
- Benchmarking operational losses
- Reporting operational losses as a percentage of gross income, of total cost, total budget, or in basis points of capital facilitates the comparability.
- No averages because of its asymmetric distributions
- Averages hide the heterogeneity. The bias in operational loss averages is often caused by outliers.
- Better alternatives to averages are the median and the first and third quartiles of the distribution.
- Combined assurance: The three lines of defense should work together to provide combined assurance to the board (RAG).
Aggregating qualitative risk data
- The challenge is that risk scores, color ratings, and other indicators are discrete, qualitative, unfit for arithmetic treatment. Solution includes:
- Conversion and addition
- Categorization
- Worst-case reporting
- Conversion and addition: Convert qualitative metrics into monetary unit that is linear, additive arithmetically.
- Categorization: Grouping them by color or score avoids the misleading collapse of heterogeneous information into improper aggregate.
- Worst-case reporting: Conservatism and prudent form,appropriate when risk tolerance is minimal, disadvantage is potentially over-alarming.
External risk reporting
- Reporting to the regulator: Pillar 3, Basel regulation
- Reporting to the market and investors: risk section of the annual report
- Reporting on operational resilience and satisfying regulatory expectations
Reporting to regulators0
- Operational risk disclosure requirements include three types of information:
- Qualitative information on operational risk management
- Historical losses. Aggregate operational losses incurred over past 10 years
- Business indicator and subcomponents
- Absence of evidence is not evidence of absence: Auditor or regulator will not take a risk manager's verbal assertion as confirmation, proof is required.要验证口头声明
- Incident reporting: Besides public disclosure, financial institutions are required to notify regulators of any significant operational risk events or any breach of conduct.
- Torn between need to be compliant with the regulation and reluctance to disclose internal operational risk failures.
Reporting on operational resilience
- In March 2022, regulated financial firms in the UK entered a three-year transitional period. By March 2025, they must:
- perform mapping and testing so that they can remain within impact tolerances for each important business service.
- make the necessary investments to enable these services to operate consistently within their established impact tolerances, and report to the regulator on these elements.
Integrated isk Management
ERM framework
- Include RMC and four elements: risk governance, risk appetite, risk culture, risk capital and stress testing.
- Risk governance, culture, and appetite sets the priorities for and guides ERM.
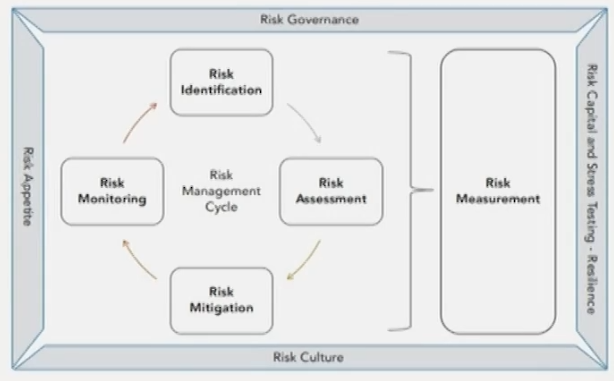
- Risk governance, culture, and appetite sets the priorities for and guides ERM.
- Risk governance
- Risk governance prescribes the roles and responsibilities of individuals in the three lines of defense, and organizes decision-making and reporting, generally through committees.
- Risk governance prescribes the roles and responsibilities of individuals in the three lines of defense, and organizes decision-making and reporting, generally through committees.
- Risk culture
- Corporate culture has a direct influence on the attitude and preferences of the firm when managing risks, from prudent to daring, from compliant to challenging.
- Regulators consider risk culture to be a key driver of ERM framework effectiveness.
- Risk appetite
- At the ERM level, risk appetite is typically expressed in overarching risk appetite statements(or policy).
Role of regulatory capital
- The objective of the BCBS prudential regulation is threefold:
- To ensure the solvency and soundness of all financial intermediaries
- To provide customers protection from undue risks (failure, fraud, opportunistic behavior)
- To promote the efficient and competitive performance of financial institutions
- Objective 1 is the primary objective, which is addressed through regulatory capital requirements.
- Objective 2 and 3 are attained through requirements on the bank's senior management's history and competence (the "fit and proper" criteria), monitoring and reporting on the bank's activities.
- However, in the United States, the focus has now shifted from capital estimation to stress testing.
- Models developed for the Federal Reserve's Comprehensive Capital Analysis and Review(CCAR) program.
- Stress testing requires institutions to estimate expected losses under specific adverse economic.
- Capital is a through-the-cycle concept, whereas stress testing is a point-in-time exercise.
Role of economic capital
- Financial intermediaries need to calculate economic capital for themselves that fully reflect their risk profile and potential needs to cover unexpected losses.
- The level of economic capital is largely linked to the credit rating, which then influences their cost of funds.
- The larger the capital, the bigger the buffer against losses,the better the creditworthiness of the institution, the lower the costs of raising funds.
Risk aggregation for capital assessment
- The aggregation of the different risk classes is the inter-risk diversification
- It supplements the intra-risk diversification, which is the diversification within each risk class.
- Total aggregated capital tends to be lower than the sum of each stand-alone capital amount for individual risk. The difference reflects the diversification benefits.
- Operational risk can bring important diversification benefits to the total capital.
- Because operational risk typically has a low correlation to other types of financial risks, due to its different risk drivers.
Stress testing
- It involves stressing that system or entity beyond normal operation, often to a "breaking point," to observe the results.
- The ultimate objective is to ensure that institutions can absorb the losses incurred under extreme adverse scenarios and remain a going concern.
- Stress testing alerts the management to adverse unexpected outcomes and provides an indication of how much capital might be needed to absorb losses.
- Dimension 1: Quantitative-Qualitative Approach
- On the quantitative end of the spectrum, stress-testing approaches relate to the sensitivity of models to parameter shocks.
- On the qualitative end of the spectrum lie approaches more focused on scenario analysis such as macro stress testing, and non-model-based evaluations like reverse stress testing.
- Dimension 2: Measurable-Immeasurable Risk
- Range from fact-based probabilistic analysis of measurable risks to more hypothetical possibilistic analysis of immeasurable risk.
- On the immeasurable risk end of the spectrum, review and analyze possible risks that are "unknown unknowns". The probability cannot be known, and it cannot be determined which event is more likely than the other.
- Parameter stress testing: to testing the robustness of a model by changing the value of its parameters.
- It utilizes quantitative approaches and seeks to analyze measurable risks.
- Banks will stress model parameters or conduct sensitivity testing to determine the impact on a particular model,portfolio, or the bank.
- Macroeconomic stress testing: It takes the most holistic view of risk run bank-wide for all risk types: seek to stress both measurable and immeasurable risks,and ideally to stress the dependency structure.
- Macroeconomic scenarios relate to infiation,unemployment rate, GDP changes and so forth, and aim at testing the financial resilience of the largest banks.
- G-SIBs (globally systemically important banks) are provided a list of macro shock scenarios to assess the solvency level.
- Parameter and macroeconomic stress testing
- Quantitative analysis of parameter stress testing focus on statistical scenarios such as a "standard deviation event".
- Quantitative analysis of macroeconomic stress testing focuses on estimating the output of the models based on a set of macroeconomic scenarios.
- Reverse stress testing
- Reverse stress testing utilizes primarily qualitative approaches and seeks to analyze immeasurable risks.
It starts from the identification of a pre-defined outcome and then determines how bad an adverse scenario would need to be to achieve the pre-defined outcome. - Reverse stress testing is a risk management tool, apt for assessing operational resilience, rather than calculating needed financial resources to weather extreme conditions.
- Reverse stress testing utilizes primarily qualitative approaches and seeks to analyze immeasurable risks.
- Operational risk stress-testing models
- In developing the macroeconomic-based stress-testing models, banks can model either total operational risk losses,or the two components of operational risk losses: frequency and severity(a preferred approach).
Severity can be more complex to model than frequency as severity is highly impacted by tail events. - Once the model produces stressed losses, an expert refinement needs to be performed using scenario analysis.
- In developing the macroeconomic-based stress-testing models, banks can model either total operational risk losses,or the two components of operational risk losses: frequency and severity(a preferred approach).
Focus Risk Areas
Cyber-Resilience
- Most jurisdictions address cyber through IT and operational risk standards.
- Even standards focusing on business continuity planning and outsourcing have relevance to cyber-risk.#### Cyber resilience standards and guidelines
- A few jurisdictions issued specific cyber-risk management guidance.
- For example, guidance in Singapore focuses on detecting cyberattacks, while guidance in Brazil focuses on establishing cybersecurity policies.
- Other jurisdictions have no specific cyber-security regulation,international standards/prescriptive guidance are encouraged.
Cyber governance

- Cyber-security strategy using three types regulatory approaches:
- Cyber-security strategy in either sector-specific or across multiple industries, common approach in emerging market.
- Individual own cyber-security strategies.
- Examining whether institution has IT strategy and accompanying security provisions, prevalent in Europe.
Approaches on cyber-risk management

Communication and sharing of information
- The content of the sharing information
- The information include cyber-threat information,information related to cyber-security incidents, regulatory and supervisory responses in case of cyber-security incidents and/ or identifications of cyber-threat, and best practices related to cyber-security risk management.
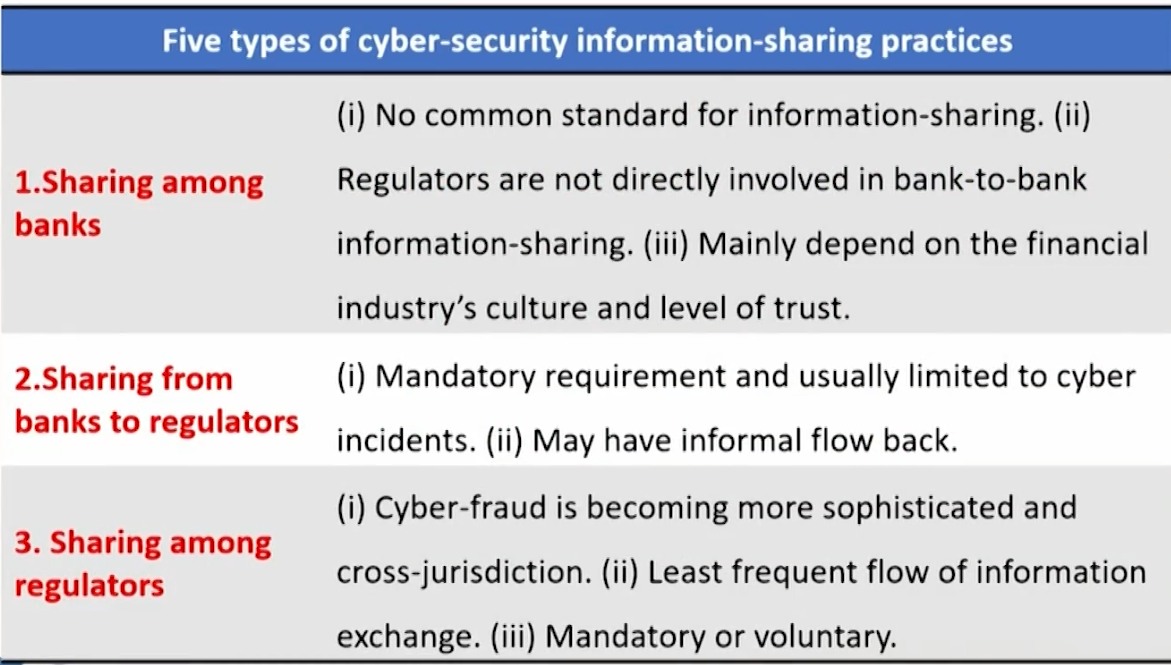

- The information include cyber-threat information,information related to cyber-security incidents, regulatory and supervisory responses in case of cyber-security incidents and/ or identifications of cyber-threat, and best practices related to cyber-security risk management.
Interconnections with third parties
- Introduction
- All jurisdictions recognize the challenge of gaining assurance of an entity's cyber-resilience, a challenge both for regulators and for financial institutions' third-party service providers.
- "Third parties" is understood in a broad sense, including:
(i) all forms of outsourcing (including cloud services);
(ii) services and products that are typically not considered outsourcing (power supply, telecommunication lines);
(iii) interconnected counterparties such as FMl.



- As regards supervisory practices, following are widespread:
- Intrusive on-site inspections relating to cyber-risk of outsourcing. The inspections review the outsourcing framework, the applicable processes and the completeness and adequacy of specific risk assessments and contracts.
- Off-site supervision, jurisdictions receive periodic reports that assess the outsourcing policies and risks.
Case Study: Cyberthreats and Information Security Risks
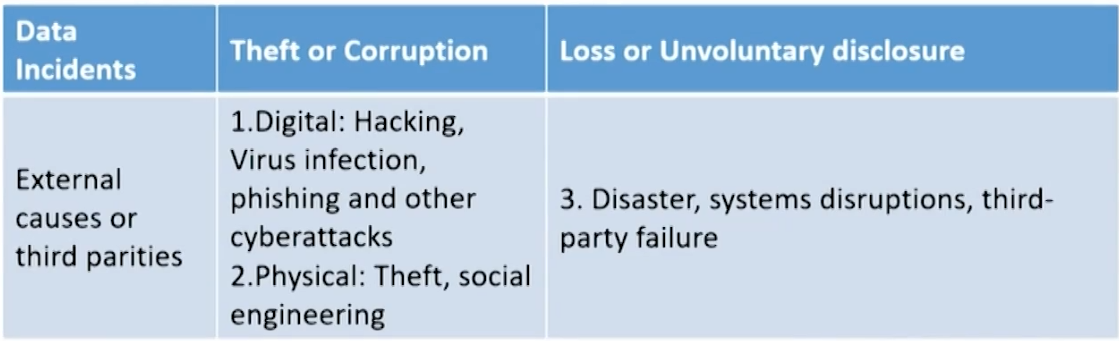
Information security risks (ISR)
- Taxonomy of IRS using a four-quadrant method:
- internal causes versus external causes
- data theft versus data loss

Cyber risk management: frameworks
- The NIST Framework for Improving Critical Infrastructure Cybersecurity
- The core of the framework is a list of cybersecurity functions that follow the basic steps of cyber defense: identify, protect, detect, respond, and recover.
- Center for Internet Security Critical Security Controls (CIS)
- CIS was built in the late 2000s by a volunteer-expert coalition to create a framework for protecting companies from the threats of cybersecurity. It is comprised of key controls, regularly updated by experts from all fields.
- CIS controls are prioritized to mitigate the most prevalent cyberattacks against systems and networks.
- ISO/lEC 27001-International Standard Organization
- The International Standard ISO/IEC 27001: 2013 is the internationally recognized standard for cybersecurity. It provides general guidance to firms to organize the risk management.
- ISO standards do not provide implementable guidance to firms per se, but rather act as evaluation grids for those who want to achieve certification in ISO standards.
Essentials of cybersecurity protection and monitoring
- The information security protection has three dimensions referred to as CIA: Confidentiality, Integrity, Availability.
- The first two relate to information security, while the third relates to business continuity and systems uptime-now in the scope of resilience.
- Information controls can be grouped into two broad categories: Behavioral controls and Technical controls.
- Behavioral controls: address human behaviors and fallibility when it comes to handling and protecting information.
- The controls include awareness campaigns, rules of conduct and prudence for employees and contractors,online training, password management, supervision, and sanctions.
- Technical controls: these relate to all technical aspects of systems, either for prevention or detection.
- Preventative controls relate to system architecture, access,firewalls, encryption, passwords and patching, and are essentially directed at external threats.
- Detective controls provide early warnings of data leaks,whether initiated internally or externally.
Equifax
- Case study
- On March 10, 2017,hackers breached Equifax's networks by exploiting a vulnerability in one of the systems via Equifax's online dispute portal.
- Attackers quickly moved from the infected portal and gained access to other parts of Equifax's network.
- For three months, hackers remained undetected while accessing multiple Equifax databases and extracting consumers' personal information.
- Lessons learned from the Equifax case study
- A lack of a comprehensive inventory of IT assets.
- Failure of risk management policy enforcement and failure to enforce the patch management policy.
- Inconsistent communication among employees on the remediation of security vulnerabilities.
- An expired SSL certificate designed to inspect encrypted network traffic
- Poor external communication as part of crisis management.
Management of Risks associated with ML and FT
Best practices
- Basel Committee is issuing guidelines to describe how banks should include money laundering (ML) and financing of terrorism (FT) risks within their overall risk management.
- The Committee has a long-standing commitment to promote the implementation of sound Anti-Money Laundering and Countering Financing of Terrorism (AML/CFT) policies and procedures that are critical in protecting the safety and soundness of banks and the integrity of the international financial system.
- To implement sound Anti-Money Laundering and Countering Financing of Terrorism (AML/CFT) policies and procedures,banks should not establish a threshold transaction value and review all transactions above the threshold.
- Terrorist screening is not a risk-sensitive due diligence and should be carried out irrespective of the risk profile. A bank should freeze without delay and without prior notice funds or other assets of designated persons and entities.
- Three lines of defense of mitigating ML and FT
- First line of defense is business units, they must identify,assess and control the risks of their business.
- Second line of defense is the chief AML/CFT officer who should have direct reporting lines to board. The chief AML/CFT officer should be the contact point regarding all AML/CFT issues for internal and external authorities,including supervisors or financial intelligence units.
- Third line of defense: Internal and/or external auditors.
- Enhanced due diligence may be required for:
- An anonymous account with large balance.
- Large size of cross-border transaction account.
- An account of foreign politically exposed person(PEP).
- A bank should not open an account with a customer who insists on anonymity (匿名), while confidential numbered accounts can not function as anonymous accounts.
- Even if a customer has opened a bank account at a reputable bank, he can not be categorized as low-risk and well-identified. Banks must perform due diligence before performing any transaction.
- While the transfer of funds from an account in the customer's name in another bank subject to the same CDD standard as the initial deposit may provide some comfort, a bank should nevertheless conduct its own due diligence.
- If a bank has any reason to believe that an applicant has been refused by another bank due to concerns over illicit activities,it should consider classifying this applicant as higher-risk and apply enhanced due diligence procedures.
- Automated processes should be employed more frequently to manage ML/FT risk as the bank involves more complicated banking business.
- Regulators encourage rather than discourage financial institutions to apply advanced analytics like machine learning which can help facilitate the detection of anomalies.
- The bank providing correspondent banking services(代理银行服务) to extensively numerous respondent banks tends to increase its ML/FT risk.
- A bank performing business nationally and abroad should appoint a chief AML/CFT officer for the whole group.
- Where the minimum regulatory or legal requirements of the home and host countries differ, offices in host jurisdictions should apply the higher(stricter) standard of the two.
- To effectively manage the ML and FT risks arising from related accounts, a bank should integrate this information based not only on the customer but also on its knowledge of both the beneficial owners of the customer and the funds involved.
Case Study: Financial Crime and Fraud
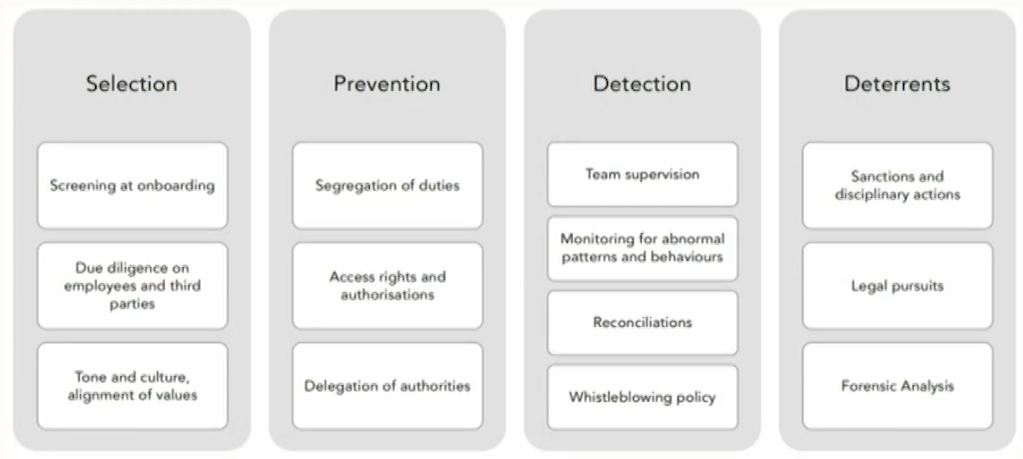
Financial fraud risk management
- Elements of a control framework to manage internal fraud.
AML risk management
- The three phases in money laundering are placement,layering, and integration or extraction.
- Elements of a control framework to manage AML risk:
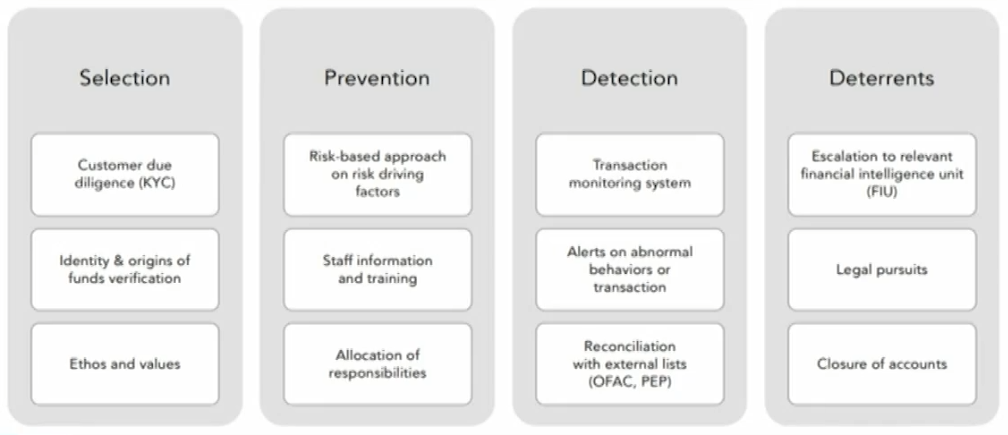
Case study: USAA
- USAA paid $140 million of fines in AML management failure reached with the Financial Crimes Enforcement Network (FinCEN) and the Office of the Comptroller of the Currency (OCC).
- The fines were due to a lack of control over AML risk(weak control environment).
- Regulatory findings and sanctions mean costly AML remediation programs (called lookbacks) in which the bank must review all client files for a specified period, verify client information, file suspicious activity reports and even close suspicious accounts.
- COVID-19 pandemic makes it more difficult for financial institutions to identify anomalies based on automation of detection prone to false positives, false negatives.
Guidance on Managing Outsourcing Risk
Risks from the use of service providers
- Compliance risks arise when a service provider violates laws/regulations.
- Concentration risks arise outsourced services are provided by limited service providers or in limited geographic locations.
- Reputational risks arise bad performance of a service provider causes the public to have negative opinion on financial institution.
- Country risks arise financial institution engages a foreign service provider, exposing possible risks from the foreign country.
- Operational risks
- Legal risks arise when a service provider exposes a financial institution to legal expenses and possible lawsuits.
Elements of effective program to manage outsourcing risk
- Risk assessments
- Due diligence and selection of service providers
- Contract provisions and considerations
- Incentive compensation review
- Oversight and monitoring of service providers
- Business continuity and contingency plans
Due diligence of service providers
- Financial institution should conduct an evaluation of and perform the necessary due diligence for a prospective service provider prior to engaging the service provider. The overall due diligence process includes a review of the service provider with regard to three points.
- Business background, reputation, and strategy
- Financial performance and condition
- Operations and internal controls
Contract provision
- Scope: contracts clearly define the rights and responsibilities of each party.
- Cost and compensation: contracts describe the compensation, variable charges, and any fees to be paid for non-recurring items and special requests.
- Right to audit: agreements provide for the right of the institution to audit the service provider/access to audit reports. The provision is optionally included.
- Establishment and monitoring of performance standards: agreements define measurable performance standards for the services or products being provided.
- Confidentiality and security of information: service providers ensure the security and confidentiality of both the institution's information and customer information.
- Ownership and license: Agreements should address the ownership of any information generated by service providers. Agreements define circumstances under which service providers may use institution property inclusive of data, hardware, software, and intellectual property.
- Indemnification赔偿: agreements provide for service provider indemnification of the institutions for any claims against the institutions resulting from the service provider's negligence.
- Default and termination: agreements define events of a contractual default, list of acceptable remedies, and provide opportunities for curing default. Bad performance and nonperformance of duties detected by performance metrics can lead to default and termination.
- Dispute resolution解决纠纷: dispute resolution process is to expedite problem resolution and minimize disruption.
- Limits on liability: service providers may want to contractually limit their liability.
- Insurance: service providers have adequate insurance and provide financial institutions with proof of insurance.
- Customer complaints: agreements specify the responsibilities of both parties related to responding to customer complaints.
- Business resumption and contingency plan of the service provider: the contingency plan is developed by the service provider and reviewed/tested by the financial institution.
- Foreign-based service providers: the institutions should consider including choice of law and jurisdictional provisions. This would avoid confusing situations where the foreign laws differ substantially from local laws.
- Banks may apply different standards for local and foreign-based service providers.
- Service agreements with foreign-based vendors should always be flexible to allow the laws of home or host country to apply for resolving related disputes.
- Subcontracting分包: if agreements allow subcontracting, the same contractual provisions should apply to subcontractor.Service providers rather than financial institutions have overall accountability负全部责任 for all services that the service provider and its subcontractors provide.
Case Study: Third-Party Risk Management
Third-party risk
- Financial firms contract with third parties for services as a cost-savings approach, outsourcing a wide variety of activitie to specialized firms with a competitive advantage in particula systems, processes, and knowledge.
- While contracting with third-party providers for back-office activities or cloud-based data management may have the potential to reduce process errors or cybersecurity risks, it does not fully mitigate operational risk and increases exposure to "third party risk".
Effective third-party risk management framework
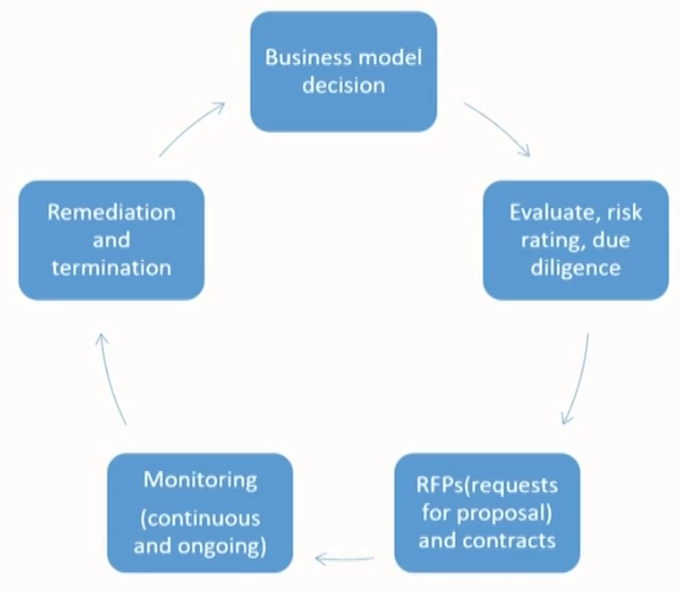
Case study: Capital One data breach
- Case: Federal authorities ultimately arrested a former Amazon Web Services (AWS) cloud services employee for breaking into the bank's server. The former employee of AWS was charged with stealing 140,000 Social Security numbers and 80,000 bank account numbers in the breach.
- Lessons: The increase in breaches involving cloud databases and services is the result of poor security hygiene.
Case study: OCC fines Morgan Stanley
- Case: Morgan Stanley received a $ 60 million fine imposed by the OcC due to failures in the risk management and oversight of vendors in the decommissioning废弃 of two wealth management business data servers in 2016.
- Lessons: The bank did not exercise adequate due diligence in selecting the third-party vendors and did not adequately monitor the vendors' performance.
Case Study: Investor Protection and Compliance Risks in Investment Activities
MIFID (Markets in Financial Instruments Directive)

Dodd-Frank
- The Investor Protection Act in the USA in 2009.
- Whistleblowers are granted increased protections.
- Mandate derivatives need to be traded in clearinghouses.
- Aim at ensuring a greater financial stability of the markets.
- The Volcker Rule intends to prevent commercial banks from engaging in speculative activities and proprietary trading.
- Create Consumer Financial Protection Bureau(CFPB).
Statistics and record fines cases
- The most severe penalty was imposed on UBS for $ 11.15 billion in 2008 because UBS misrepresented auction rate securities to investors as safe, cash-equivalent products,when in fact they faced increasing liquidity risk.
- The largest fine for spoofing is held by JP Morgan谎骗下单,下单又取消 fined $ 920 million by the CFTC(Commodity Futures Trading Commission) in September 2020 by US regulators for "spoofing" in the precious metals and US Treasury markets.
FINRA fines Deutsche bank securities
- The Financial Industry Regulatory Authority(FINRA) fines Deutsche bank securities, Inc. $ 2 million for best execution violations.
- FINRA found that, between 2014 and 2018, Deutsche Bank Securities was routing customer orders to exchanges through its smart order router. This indirect routing of orders created delays of execution in customers' market orders and also caused lower fill rate.
- Lessons:
- Regulators tend to apply punitive fines such that the penalty more than offsets the benefits accumulated where firms perpetuate non-compliant practices.
- The fines are aimed to act as deterrent for further deviations and have a signaling power to peer firms to encourage them to adjust their processes and monitoring practices to ensure compliance.
Supervisory Guidance on Model Risk Management
Model risk
- Model refers to a quantitative method, system, or approach that applies statistical, economic, financial, or mathematical theories, techniques, and assumptions to process input data into quantitative estimates.
- A model consists of three components:an information input component; a process component; a reporting component.
- Models are simplified representations of real-world, focus on particular aspects considered to be most important.
- Model risk
- Model risk: the potential for adverse consequences from decisions based on incorrect or misused model outputs/reports.
- Model risk occurs for two reasons
- Fundamental errors produce inaccurate outputs against the design objective and intended business uses.
- The model may be used incorrectly or inappropriately.
Effective framework to manage model risk
- Elements of the framework
- Robust model development, implementation, and use
- A sound model validation process
- Governance sets an effective framework with defined roles and responsibilities, as well as the authority to restrict model usage.
- Development,implementation
- At initiation, ensure the model is logical and is on the basis of technically-correct mathematical theories.
- Then ensure that the data collected and assumptions are robust and relevant for the model.
- Finally there should be a clear documentation and made clear to users.
- After developing the model:
Quantitative aspects: quantitative model testing includes checking the model's accuracy, robust and stable, limitations and the model's assumption/behavior over a range of input values. Testing should be done in both normal and extreme (stressed) market conditions.
Qualitative aspects: Banks should ensure that the development of the more judgmental and qualitative aspects of their model is also sound.
- validation
- Evaluation of conceptual soundness稳健性, including developmental evidence Carry out overall quality check on the model design and construction.
Mainly examine the documentation evidence and perform supplemental sensitivity analysis(one variable change) and testing (multiple variables change)
Qualitative information and judgment in model development should be validated and documented. - Ongoing monitoring, including process verification and benchmarking
Once the model comes into play, ongoing monitoring begins. Ongoing monitoring tries to determine whether any changes, additional developments, or replacement should be needed for the model.
Sensitivity analysis and other checks for robustness and stability should likewise be repeated periodically.
Ongoing monitoring should include the analysis of overrides修改 with appropriate documentation. - It includes process verification and benchmarking to confirm the model is implemented as intended.
Process verification: Ensure data inputs to be error-free and complete.Execute Internal control to ensure computer code can only be altered by authorized staff.
Benchmarking: Compare a model's outputs with other comparable models or inputs with comparable data. Discrepancies should trigger investigation into the sources and degree of the differences. - Outcomes analysis, including back-testing
Rely on quantitative approaches such as statistical tests and qualitative approaches such as expert judgment.
Outcomes analysis should be conducted on an ongoing basis. Confidence intervals need to be developed based on the model estimates, so that outcomes that are beyond the intervals should be specially focused on and monitored.
Parallel outcomes analysis is based on that models are frequently revised for new information or data.
- Evaluation of conceptual soundness稳健性, including developmental evidence Carry out overall quality check on the model design and construction.
Challenges to an effective validation process
- System integration can be a challenge because the model need draw from various sources of data to process huge data,and feeds into multiple data repositories and reporting systems. 数据获取困难
- The widespread use of vendor/third-party products poses unique challenge because the modeling expertise is external to the user and some components may considered proprietary独有. 使用人不知道原始算法
Case Study: Model Risk and Model Validation
Model risk
- There are two broad risks an institution can be exposed to due to model risk.
- Execution risk: occurs when a model does not do what it is intended and designed to do.用错地方
- Conceptual errors: occur when the wrong assumptions or modeling techniques are used in the model.模型本身有错
- Model risk management(MRM) function
- MRM function sits in the second line of defense and is staffed with experts who are independent of model development.
- To balance the cost and burden of model validation with the need to ensure that model risk is adequately addressed, MRM functions assign models to different tiers according to the risk they pose to the institution.
Highest-tier models will be reviewed in detail, with the validation team performing comprehensive back-testing and assessing the model.
High-tier models also undergo more frequent full scope validations, usually every 2 to 3 years.
Lower-tier models are subject to a similar process but with the depth and frequency of the various actions tailored to the tier. - All models, independently of their tier, undergo an annual review of the environment.
- Model risk management should be seen as a continuous effort rather than a point-in-time exercise revolving around validations and reviews.
Gaussian Copula and CDO pricing
- Case: Correlation assumption is a problem.Banks fail to update the copula model with the new correlation estimates implied by new CDS prices, and continue to price CDOs using the old assumptions.没有更新系数
- Lessons: The critical responsibility of MRM function is to challenge the assumptions upon which the model relies and ensure that users understand its limitations.
Barclays' acquisition and excel spreadsheet error
- Case: Barclays Capital offered to acquire Lehman Brothers' positions after Lehman Brothers filed for bankruptcy,including 179 trading contracts that Barclays did not want to buy. They were hidden rather than deleted. A junior law associate reformatting the Excel file to a PDF makes hidden rows visible again in the PDF file.没发现隐藏的数据
- Lessons: Seemingly simplistic tools or models still need the right review, challenge and controls.
NASA Mars Orbiter
- Case: NASAlost a $125 million Mars orbiter because a Lockheed Martin engineering team used English units of measurement, while the agency's team used the more conventional metric system. 采用的单位不匹配
- Lessons: This is an error in the "assumptions" of the model the choice of the unit (metric vs imperial). A small subset of these mistakes can result in catastrophic losses ($125 million).
Capital Planning
Risk Capital Attribution & Risk-Adjusted Performance
Risk capital, economic capital, & regulatory capital
- Risk capital is the cushion that provides protection against the various risks (i.e., unexpected loss) inherent in the business of a corporation so that the firm can maintain its financial integrity and remain a going concern even in the event of a near-catastrophic worst-case scenario.
- Risk capital is often called economic capital, and in most instances the generally accepted convention is that risk capital and economic capital are identical.
- Regulatory capital
- First, regulatory capital applies to regulated industries to protect the interests of small depositors or policy holders.
- Second, regulatory capital is calculated by regulatory rules and formulas and sets a minimum required level of capital adequacy.
- Third, even if regulatory and risk capital are similar numbers, they may not be similar for each constituent business line.
- Uses of economic capital-traditional way: Economic capital is really important to financial institutions.
- Capital is primarily used in a financial institution not only to provide funding but also to absorb risk.
- A bank's target solvency is a vital part of the product the bank is selling.
- Although bank creditworthiness is critical, banks are also highly opaque institutions.
- Banks operate in highly competitive financial markets.
- Uses of economic capital-new way: Economic capital's new uses including
- Performance measurement and incentive compensation at the firm, business unit, and individual levels
- Active portfolio management for entry/exit decisions
- Pricing transactions: calculate risk-based pricing for individual transactions. Each transaction considers the expected loss and the cost of economic capital allocated.
RAROC: risk-adjusted return on capital
- RAROC = after-taxexpected risk-adjusted net income / economic capital
- After-tax expected risk-adjusted net income = expected revenues - costs - expected losses - taxes + return on risk capital +/- transfers
- Expected revenues are the revenues that the activity is expected to generate (assuming no losses).
- Costs are the direct expenses associated with running the activity.
- Expected losses are also called PD amount, they correspond to the loan loss reserve (or provision) that the bank must set aside as the cost of doing business.
- Taxes are the expected amount of taxes imputed to the activity using the effective tax rate of the company.税基为所有收入 - 所有成本
- Return on risk capital is the return on the risk capital allocated to the activity. It is generally assumed that this risk capital is invested in risk-free securities.
- Transfers correspond to transfer pricing mechanisms,primarily between the business unit and the treasury司库 group, such as charging the business unit for any funding cost incurred by its activities and any hedging cost.银行整体的Transfers为0,部门不一定
- Economic capital = risk capital + strategic capital = risk capital + goodwill + burned-out capital
- Strategic risk capital refers to the risk of significant investments about whose success and profitability there is high uncertainty
- Burned-out capital refers to the idea that capital is spent on the initial stages of starting up business, but the business may ultimately fail.
- Goodwill is the amount paid above the replacement value of the net assets (assets - liabilities) when acquiring a firm.
RAROC calculation issues
- Time horizon choice for RAROC is somewhat subjective.
- PD is used for economical capital calculation on an anticipatory or ex ante basis.
- A point-in-time (PIT) PD is reasonable for near-term expected losses and individual financial instrument.
- A through-the-cycle (TTC) PD is more reasonable for economic capital, current profitability, and strategic decisions.
- PIT is more volatile than TTC.
- Confidence level: setting a lower confidence level may reduce the amount of risk capital allocated to an activity.
- Lower confidence level → Lower economic capital → Higher RAROC → Affect capital allocation decisions(allocating risk capital to business units and individual transactions for the purpose of measuring economic performance)
Once capital has been allocated, each business unit manages its risk so that it does not exceed its allocated capital. - The confidence level in economic capital calculation should be consistent with firm's target credit rating and can be regarded as a quantitative expression of the risk appetite of the firm.
Business units tend to apply lower confidence levels than the firm-wide target confidence level.
- Lower confidence level → Lower economic capital → Higher RAROC → Affect capital allocation decisions(allocating risk capital to business units and individual transactions for the purpose of measuring economic performance)
RAROC for capital budgeting decision
- Hurdle rate (H_{AT}) is after-tax weighted average cost of equity capital to compare with RAROCto make investment decision.
h_{A T}=\frac{C E \times R_{C E}+P E \times R_{P E}}{C E+P E}- C E / R_{C E} and P E / R_{P E} is the value/cost of common equity and preferred equity, respectively.
- If RAROC > hurdle rate, add value to the firm, the project should be accepted.
- If RAROC < hurdle rate, destroy value for the firm, the project should be rejected or closed down.
- ARAROC: Adjusted RAROC
ARAROC = RAROC -\beta_{C E}\left(\bar{R}_M-r_f\right)- \bar{R}_M is the expected return on the market portfolio, \beta_{C E} is the beta of the equity of the firm.
- ARAROC > r_f: Accept projects
- ARAROC < r_f: Reject projects
- Risk capital and diversification: risk capital for the firm should be significantly less than the sum of the stand-alone risk capital of the individual business units due to diversification.
- Stand-alone capital is the capital used by mutual independent view among business units.
- Fully diversified capital is the capital attributed to each activity X and Y, considering diversification from combining.
- Marginal capital is the additional capital required by an incremental business, considering diversification.
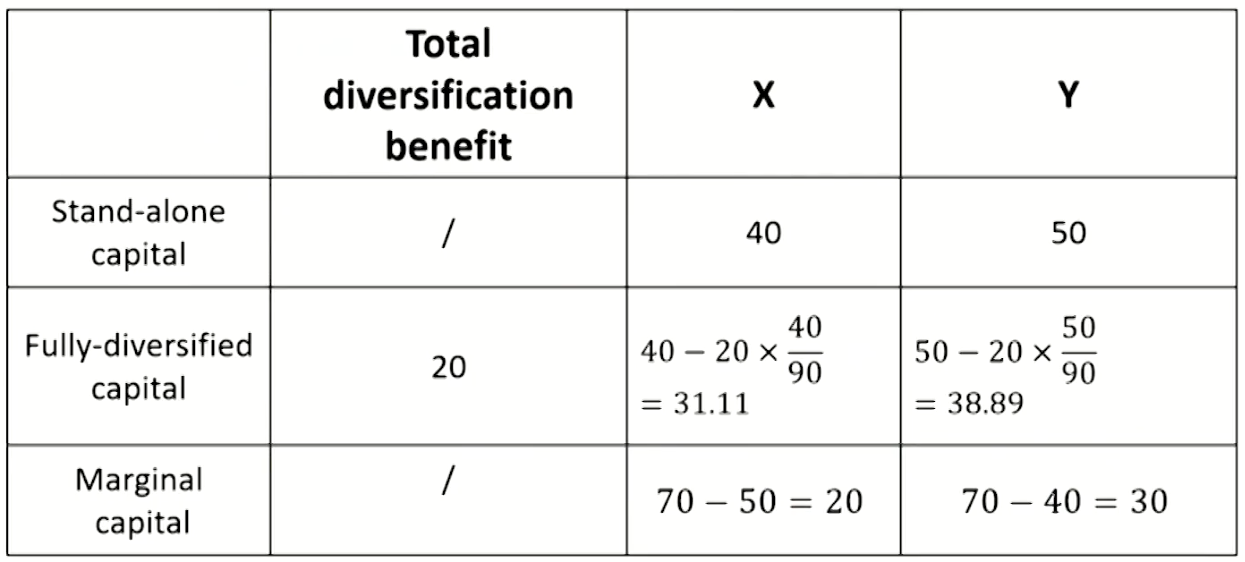
Range of practices and issues in economical capital framework
Overview of economical capital framework
- Economic capital has broadened to combine the underlying risks (building blocks) into an overall aggregation. The building blocks:
- Use of economic capital and governance
- Risk measures
- Risk aggregation
- Validation of economic capital
- Dependency modelling in credit risk
- Counterparty credit risk
- Interest rate risk in the banking book
- governance
- Senior management need to provide credible commitment,recognize the importance of using economic capital measures, put adequate resources and fully understand the limitations of economic capital measures.
- risk measure
- Banks use a variety of risk measures such as VaR and ES
- All risk measures have advantages and disadvantages which need to be understood within the context of their intended application.
- risk aggregation
- Practices and techniques in risk aggregation are generally less sophisticated更简单 than the methodologies that are used in measuring individual risk components.
- Since individual risk components are typically estimated without much regard to the interactions between risks (e.g.,between market and credit risk), the aggregation methodologies used may underestimate overall risk even if ""no diversification" assumptions are used.
- There are five commonly used aggregation methodologies.
Simple summation: assumes equal weighting, does not take into account the diversification benefits (p = 1).
Constant diversification: subtracts a fixed diversification percentage from the overall amount.
Variance-covariance matrix: Estimates of inter-risk correlations are difficult and costly to obtain. It does not adequately capture nonlinearities and skewed distributions, leading to underestimate the risk.
Copulas: combines marginal probability distributions into a joint probability distribution. It offer greater flexibility in the aggregation of risks and promise a better approximation of the true risk distribution. More demanding input and building a joint distribution is very difficult.
Full modeling/simulation: simulates the impact of common risk drivers on all risk types and construct the joint distribution of losses. Theoretically, the most appealing method, potentially the most accurate method. High information technology demands, the process is time consuming, and it may provide a false sense of security.
- validation
- The validation of economic capital models is at a very preliminary stage. There exists a wide range of validation techniques, each of which provides evidence for (or against only some of the desirable properties of a model.
- dependency modeling
- A particularly important and difficult aspect of portfolio credit risk modelling is the modelling of the dependency structure,both linear and non-linear relationships between obligors.
- The main concern in the area continues to center on the accuracy and stability of correlation during times of stress.
- The correlation estimates provided by current models still depend heavily on explicit or implicit model assumptions.
- counterparty credit risk
- Measurement of counterparty credit risk represents a complex exercise, as it involves gathering data from multiple systems, millions of transactions, time horizons ranging from overnight to thirty or more years, tracking collateral and netting arrangements, thousands of counterparties.
- This complexity creates unique market-risk-related challenges and operational risk-related challenges.
- interest rate risk
- The main challenges for interest rate risk in the banking book is the long holding period for balance sheet and modeling indeterminate cash flows due to embedded optionality in many banking book items.
- If not adequately measured and managed, the asymmetrical payoff characteristics of instruments with embedded features can present risks that are significantly greater thanthe risk measures suggest.
Recommendations
- Use economic capital model in assessing capital adequacy: A bank demonstrates how economic capital model is integrated into business decision-making process and understanding of gap between gross (standalone) and net (diversified) risk.
- Senior mgt: credit commitment to ensure meaningfulness/integrity of process and adequate resources.
- Transparency and integration into decision making
- Risk identification: not all risks can be directly quantified.
- Risk measures: no singularly preferred risk measure.
- Risk aggregation: depends on quality of the measure of individual risk components and interactions between risks.
- Validation: Validation should ensure the capital generated by the model is sufficient and model is fit for purpose.
- Dependency modeling in credit risk: using adequate supplementary approaches (sensitivity analysis, scenario analysis) to address the limitation of credit models.
- Counterparty credit risk: complementary measurement processes such as stress testing should be used.
- Interest rate risk in banking book: close attention to the instruments with embedded option, which can present significant risk.
Benefits and impacts of EC using and governance
- In order to achieve a common measure across all risks and businesses, economic capital is often parameterized as an amount of capital that a bank needs to absorb unexpectedlosses over a certain time horizon at a given confidence level.
- Because expected losses are accounted for in the pricing of a bank's products and loan loss provisioning, it is only unexpected losses that require economic capital.
- Credit portfolio management
- Benefit
Economic capital is a measurement of the level of concentration. A credit's incremental risk contribution is used to determine the concentration of the credit portfolio.
The bank allocates economic capital according to the credit asset's marginal contribution to the bank's total portfolio risk rather than its standalone risk - Impact
Credit portfolio management allows banks to specify appropriate hedging strategies to reduce portfolio concentration, protecting against risk deterioration.
- Benefit
- Risk-based pricing
- Benefit
In theory, under the assumption of competitive markets,prices are exogenous to banks acting as price-takers. Decisions are driven by a floor/threshold (the minimum RAROC) computed according to the amount of economic capital allocated to the deal. - Impact
Exceptions(specific customer relationship/reputational side-effect) to the rule are strictly monitored and require the decision be elevated to a higher level of management.
- Benefit
- Customer and product profitability analysis
- Benefit
The measurement of performance can be extended down to the customer level, through the analysis of customer profitability to provide the relative risk-adjusted profitability of customer relationships and products. - Impact
Segmenting customers and resources re-allocating based on more efficient profitable relationships.
- Benefit
- Management incentives
- Benefit
Economic capital could affect the objective functions of decision-makers at the business unit level and be used in the incentive structure for business-unit management. - Impact
Incentives are the most sensitive element for a majority of bank managers and motive them involved in the technical aspects of the economic capital allocation process
RAROC can motivate business unit managers by enhancing their incentive compensation as less economic capital is allocated to their respective business unit.
- Benefit
Capital Planning at Large Bank Holding Companies
Overview of Fed capital plan rule
- Federal Reserve's Capital Plan Rule requires all U.S.BHCs to have a capital plan by a robust capital adequacy process. The capital plan covers all U.S. domiciled BHCs with total consolidated assets equal to $50 billion or more.
- Foundational risk management:The BHC has a sound risk-measurement and risk-management infrastructure to support identification, measurement, assessment and control of all material risks.
- Stronger risk-identification practices include standardized processes (regularly update, review risk exposures).
- Lagging practice: did not try to account for reputational risk, strategic risk and compliance risk.
- Loss-estimation methodologies:The BHC has processes for translating risk measures into estimates of losses over a range of stressful scenarios and for aggregating those estimated losses across the BHC.
- Apply conservative approaches to estimate losses.
- Stronger scenario-design practices have clear narrative describing the vulnerabilities/material risks the firm facing.
- Stronger scenario-design practices used internal models in combination with expert judgment rather than relying solely on either.
- BHCs can use third-party scenarios with stronger practices tailoring third party-defined scenarios to their own risk profiles and unique vulnerabilities.
- Leading practice: In evaluating modeling program of BHC,BHC should strive to estimate loss models at granular level.细化估计
- BHCs should use internal operational-loss data as a starting point to provide historical perspective, and then incorporate forward-looking elements, idiosyncratic risks,and tail events to estimate losses.
- Lagging practice: model the loss given default of the bank's loan portfolio using a weighted-average approach at the aggregate portfolio level. Leading practice clearly tied LGD to underlying risk drivers.
- BHCs with leading practices used automated processes,while BHCs with lagging practices exhibited a high degree of manual intervention in the aggregation process.
- By design, estimates based on long-run average behavior,including periods of economic expansion and downturn,are not appropriate for projecting losses under stress.
- It is weak to combine two models: roll-rate model and net charge-off model.
- Resource-estimation methodologies:The BHC has a clear definition of available capital resources.
- Quantitative basis and qualitative projections (expert judgment);
- Conservatism and credibility;
- Documentation.
- Capital policy and capital planning:BHC has capital policy for establishing capital goals, capital levels and composition of capital, making decisions about capital actions, and setting capital contingency plans.
- BHC should establish capital targets above capital goals.
- Contingency actions should be flexible enough and realistic for what is achievable during periods of stress.
- Lagging practice: establish triggers based on actual results but not on projected results, or based on minimum regulatory capital ratios.基于预测结果出发应急预案最好
- Assessing capital adequacy impact:The BHC has processes for estimating of losses and capital resources to assess impacts on capital adequacy.
- BHCs should have a process for projections of the size and composition of on/off-balance sheet and RWA.
- Balance projections are a key input to enterprise-wide scenario analysis given direct impact on the estimation of losses, PPNR(pre-provision net revenue), and RWA.
- Use a full-revaluation approach to model the bank's non-linear positions (such as complex derivative exposures).
- Internal controls:The BHC has robust internal controls governing capital adequacy process components, including policies and procedures; change control; model validation and independent review; comprehensive documentation; and review by internal audit.
- BHCs should ensure that validation covers all models and assumptions used for capital planning purposes, including any adjustments management has made to the model estimates (management overlay).
- Governance: The BHC has effective board and senior management oversight of the capital adequacy plan ( CAP).
- Board has final oversight accountability for capital planning and should receive related information at least quarterly.
- Senior management is responsible for ensuring that capital planning activities authorized by the board are implemented in a satisfactory manner and is accountable to the board for the effectiveness of those activities.
Stress Testing Banks
Stress testing- historical evolution
- Supervisory capital assessment program (SCAP) is a US bank stress test in 2009.
- A successful macro-prudential stress testing program, also the first macro-prudential stress test after the 2007-2008 financial crisis.
- Macro-prudential focuses on the soundness of the banking system as a whole (systematic risks), but micro-prudential focuses on the soundness of the individual institution.
- The 2009 SCAPtested macro scenarios with three main variables: growth in GDP, unemployment rate, and the house price index(HPI).
- SCAP has at least two components:
- Assessment of institutions: capital strength vs. capital "hole" that needs to be filled
- A credible way of filling that hole可以发股票填补漏洞
- Features of stress testing, pre-and post-SCAP
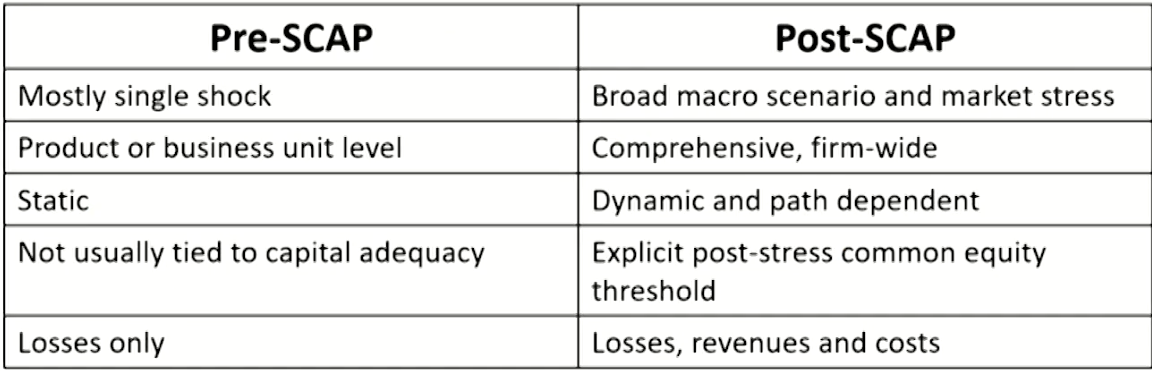
- Before 2011 all supervisory stress tests applied the same scenarios on all banks (i.e., one-size-fits-all approach一刀切).
- Mechanically uniform approaches pose problems, so the2011 and 2012 CCAR(Comprehensive capital analysis and review) asked banks to submit results from banks'own stress scenarios (baseline and stress) besides the supervisory stress scenario in order to bring banks' own vulnerabilities to light.考虑银行个性
- 2011 CCAR required that only the macro scenario was published (disclosed), but no bank level results.
- 2012 CCAR disclosed nearly the same level of detail as the 2009 SCAP, namely bank-level loss rates and dollar losses by major regulatory asset class.
- Disclosure was an important trait of the 2009 SCAP.
Before 2009 SCAP: disclosed realized losses
After 2009 SCAP: disclosed projected预测值 losses
- Disclosure was an important trait of the 2009 SCAP.
- 2011 European banking authority(EBA) conducts European stress test.
- The EBA test includes both a baseline scenario and a stress scenario.
- The EBA also required significant disclosures. The disclosure was more extensive, including information on exposure by asset class and by geography. All bank level results were available to download in spreadsheet form.
Stress testing-challenges in designing scenarios
- Principal challenges in designing stress scenarios is coherence,especially inherently multi-risk factors, making it more difficult to design a coherent stress test.jiaxiang
- The supervisor's key challenge is to state the joint outcomes of inherently multi-risk factors.
- Not everything becomes terrible simultaneously.
Currency depreciation vs.currency appreciation, riskier asset vs. safe haven assets (flight to quality).
- From macro-scenario to micro-outcome: losses/revenues,the first task is to map from the few macro-factors into the many intermediate risk factors that drive losses.
- In a stress model, the starting balance sheet generates first quarter's income and loss, which in turn determines quarter-end balance sheet. The bank must maintain its capital and liquidity ratios level during all quarters of the stress test time horizon, typically for two years